Akira Ransomware: A Rising Cybersecurity Threat
The cybersecurity threat landscape is evolving like a wildfire, and the latest threat to emerge is the Akira Ransomware. This malicious software has been causing significant concern worldwide, targeting both Windows and Linux-based systems, much like the Mallox Ransomware The Indian Computer Emergency Response Team (CERT-In) has issued a warning about this new internet Ransomware virus, which is known for its double extortion tactics.
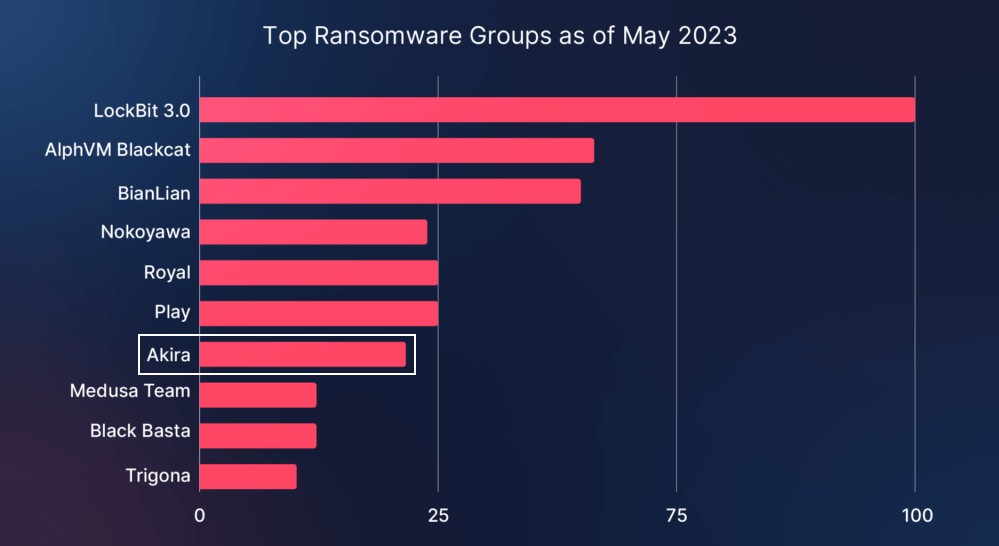
What is Akira Ransomware?
Akira is a new family of Ransomware that first emerged in the U.S. and Canada in March this year. Unlike other Ransomware threats, Akira uses a double-extortion technique to exfiltrate and encrypt data, increasing the chances of extracting money from its victims. The Ransomware has already impacted numerous organizations, with 80% of its victims being small to medium-scale businesses.
Read also: SMBs under Attack – Struggle with Exploits, Trojans and Backdoors
Akira Ransomware is designed to encrypt data, create a Ransomware note, and delete Windows Shadow Volume copies on affected devices. It modifies filenames of all the encrypted files by appending them with the “.akira” extension. The Ransomware is designed to close processes or shut down Windows services that may interfere with its encryption process. It uses VPN services, especially when users have not enabled two-factor authentication, to trick users into downloading malicious files.
How Does Akira Work?
Once Akira infects a device, it steals and encrypts sensitive data. The Ransomware group behind the attack then extorts the victims into paying a ransom, threatening to release the data on dark web if their demands are not met. The Ransomware deletes the Windows Shadow Volume copies on the affected device, which are instrumental in ensuring that organizations can back up data used in their applications for day-to-day functioning. Once the Ransomware deletes the VSS files, it proceeds to encrypt files with the pre-defined the “.akira” extension.
Read also: The Anatomy of a Modern Ransomware Attack – How Does Ransomware Work?
Who Does Akira Target?
Since its inception in March 2023, Akira has targeted corporate networks in various domains, including education, finance, real estate, manufacturing, and consulting. Once it breaches a corporate network, the Ransomware spreads laterally to other devices after gaining Windows domain admin credentials. The threat actors also steal sensitive corporate data to execute their extortion attempts.
Read also: A Leading Engineering Company in Asia Hit by Ransomware Attack, Halts Operations!
How to Protect Against Akira Attacks?
CERT-In has advised users to follow basic internet hygiene and protection protocols to ensure security against Ransomware. These include maintaining up-to-date offline backups of critical data to prevent data loss in the event of an attack. Additionally, they have advised to ensure all operating systems and networks are updated regularly, with patching for legacy systems and networks.
Companies must also establish Domain-based Message Authentication, Reporting, and Conformance, Domain Keys Identified Mail (DKIM), and Sender policy for organizational email validation, which prevents spam by detecting email spoofing and callback phishing attacks. Strong password policies and multi-factor authentication (MFA) must be enforced. There should also be a strict external device usage policy in place and data-at-rest and data-in-transit encryption along with blocking attachment file types like .exe, .pif, or .url to avoid downloading malicious code. The agency has also advised periodic security audits of critical networks/systems, especially database servers.
Preventive Measures against Ransomware Attacks
Futurism recommends the following preventive measures to keep Akira and various other coming-of-age Ransomware attacks at bay:
Regular Backups: Maintain regular offline backups of all your important data. This ensures that you can restore your system to its previous state even if you become a victim of a Ransomware attack.
Software Updates: Keep all your software and systems updated. Cybercriminals often exploit known vulnerabilities in software, so keeping your software up-to-date with regular vulnerability assessment and penetration testing (VAPT) can help protect your system.
Email Attachments: Be wary of email attachments, especially from unknown senders. Many Ransomware attacks are initiated through malicious email attachments. Deploying a powerful email security solution can help greatly in averting such attacks.
Firewall and Antivirus: Use a reliable firewall and antivirus program. These can help detect and block Ransomware.
Avoid Suspicious Links: Do not click on suspicious links, whether they are in emails, text messages, or online ads.
Educate Employees: If you’re a business, educate your employees about the risks of Ransomware and how to avoid falling victim to it.
Use Strong, Unique Passwords: Using strong, unique passwords can make it harder for Ransomware to gain access to your system.
Enable Multi-Factor Authentication: Wherever possible, enable multi-factor authentication with a powerful identity and access management (IAM) solution. This adds an extra layer of security that can prevent Ransomware attacks.
Deploy Zero Trust Security: A significant number of cybersecurity strategies fall short in addressing threats originating from the dark web. Additionally, these strategies often lack the necessary intelligent threat insights. Futurism recommends implementing a Zero Trust Security Model to tackle these security issues. This framework enhances risk management by eliminating any assumed trust. Regardless of the user’s location, circumstances, identity, or the method/platform of access, Zero Trust Security Model prioritizes security. It provides operational, strategic, and intelligent insights to security administrators and IT professionals, filtering out unnecessary noise, and enabling them to react swiftly to threats.
Takeaway
By following these preventive measures, organizations can significantly reduce their risk of falling victim to Ransomware attacks like Akira. Stay one step ahead of cyber threats. Protect your mission-critical business/use data and systems now. Learn more about our advanced AI-powered cybersecurity – SIEM services here.
Don’t fall for the bait! Get help now!
Disclaimer: The information and statistics shared in this article are attributed solely to the original authors and their respective web source. They do not necessarily align with or represent the goals, beliefs, or viewpoints of Futurism Technologies.
Futurism Technologies is a trusted Digital Transformation (DX) advisor and consulting partner helping businesses around the world to unlock the true value of digital for the last two decades. One of the fastest-growing global digital transformation companies with offices across continents including North America, Europe, the Gulf, Asia, and Australia, Futurism delivers 360-degree Digital Transformation solutions to enterprises of all sizes and verticals. We have been helping enterprises leverage advanced technologies with our tested DX solutions. Futurism takes great pride in helping businesses realize the true potential of digital by helping them leverage the most from coming-of-age technologies such as Artificial Intelligence (AI), Machine Learning (ML), Robotic Process Automation (RPA), 5G, IoT, Data Science/Big Data, Cybersecurity, Blockchain, Mobility, Product Engineering, Cloud, and more.
Make your business more successful with latest tips and updates for technologies