Microsoft Warns of Increased AiTM Phishing Attacks
Microsoft has warned of a startling increase in Adversary-in-the-Middle (AiTM) phishing attacks, which are being unleashed as a part of the phishing-as-a-service (PhaaS) cybercrime model.
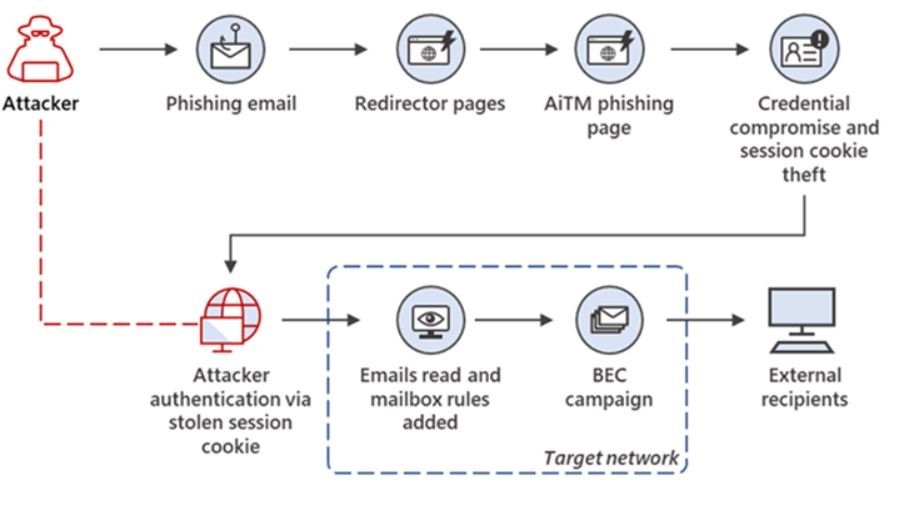
AiTM attack is a sophisticated type of phishing attack that allow attackers to steal user credentials and session cookies, even if the user has enabled multi-factor authentication (MFA). This is done by intercepting the traffic between the user’s device and the legitimate website, and then injecting malicious code into the traffic.
Microsoft has observed an increase in the number of AiTM-capable PhaaS platforms, as well as existing phishing services that are incorporating AiTM capabilities. This development in the PhaaS ecosystem makes it easier for attackers to launch large-scale AiTM phishing campaigns that can bypass MFA protections.
Read also: Cyberattack exposes 10M+ healthcare records in the U.S.
How do AiTM attacks work?
There are two main ways that AiTM attacks work:
Reverse proxy servers: In this method, the attacker sets up a reverse proxy server that acts as a middleman between the user’s device and the legitimate website. The attacker then uses the reverse proxy server to intercept the traffic between the two parties and steal the user’s credentials and session cookies.
Synchronous relay servers: In this method, the attacker sets up a synchronous relay server that is synchronized with the legitimate website. The attacker then uses the synchronous relay server to present the user with a fake login page that looks identical to the legitimate login page. When the user enters their credentials on the fake login page, the attacker is able to steal them.
What are the preventive measures against AiTM attacks?
There are a number of preventive measures that can be taken to thwart AiTM attacks, including:
Enable MFA: MFA is one of the most effective ways to protect against phishing attacks, including AiTM attacks. MFA requires users to provide two or more factors of authentication, such as a password and a one-time code, to gain access to an account.
Deploy IAM: Yes, a robust identity and access management system can deploy a powerful line of defense when it comes to who will access what through a robust risk-based authentication.
Be wary of suspicious emails: Be suspicious of any emails that you receive from unknown senders, or that contain links or attachments that you are not expecting. Do not click on any links or open any attachments in these emails. Deploying a strong email security solution can go a long way here.
Keep your software up to date: Keep your software, including your web browser and email client, up to date with the latest security patches. This will help to protect your data from vulnerabilities that can be exploited by attackers.
Seek expert help: Partner with a trusted managed security services provider that can help deploy the right layers of defense to protect AiTM phishing attacks.
Be proactive: If you think that you have been the victim of an AiTM attack, it is important to take immediate action to protect your accounts. This includes changing your passwords and enabling MFA on all of your accounts. You should also report the attack to the relevant authorities.
Get a free security assessment to see how vulnerable your organization is to AiTM phishing attacks. Contact us now.
Disclaimer: The data and insights presented in this article are the original work of the authors cited and their associated online references. Their perspectives do not necessarily reflect or endorse the values or opinions of Futurism Technologies in any way.
Futurism Technologies is a trusted Digital Transformation (DX) advisor and consulting partner helping businesses around the world to unlock the true value of digital for the last two decades. One of the fastest-growing global digital transformation companies with offices across continents including North America, Europe, the Gulf, Asia, and Australia, Futurism delivers 360-degree Digital Transformation solutions to enterprises of all sizes and verticals. We have been helping enterprises leverage advanced technologies with our tested DX solutions. Futurism takes great pride in helping businesses realize the true potential of digital by helping them leverage the most from coming-of-age technologies such as Artificial Intelligence (AI), Machine Learning (ML), Robotic Process Automation (RPA), 5G, IoT, Data Science/Big Data, Cybersecurity, Blockchain, Mobility, Product Engineering, Cloud, and more.
Make your business more successful with latest tips and updates for technologies