Introduction
The Internet of Things (IoT) has emerged as a revolutionary tech, transforming our daily lives with smart devices and interconnected technologies. From the convenience of voice-activated home assistants to the efficiency of automated industrial processes, the benefits of IoT are undeniable. However, this widespread connectivity also ushers in significant security challenges, with IoT devices becoming prime targets for cyber threats and malware attacks.
As we venture into this guide, let us not only celebrate the marvels of IoT but also confront the lurking dangers of cyber threats head-on, arming ourselves with the knowledge and tools necessary to forge a secure path forward in this interconnected world. This journey into the future of IoT security is not just about safeguarding our digital assets; it's about ensuring the enduring legacy of innovation in the face of ever-evolving cyber adversaries.
The Growing Threat Landscape
The rapid increase of IoT devices has not only simplified our lives but also expanded the chances of attack surface for cybercriminals. Recent statistics show a disturbing uptrend in IoT malware incidents, underscoring the critical need for robust security measures. These devices, often designed with convenience in mind, lack the sophisticated security mechanisms necessary to defend the advanced threats, making them susceptible to a wide array of cyberattacks.
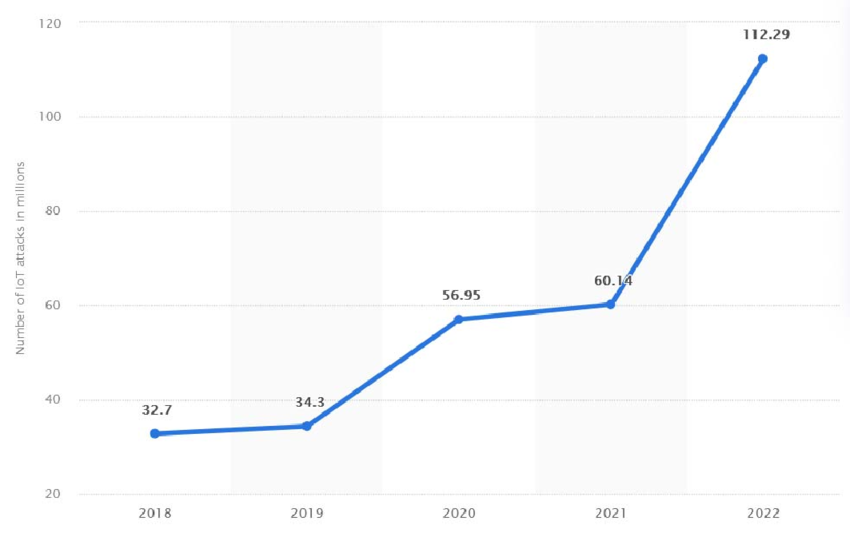
The annual number of IoT malware attacks worldwide from 2018 to 2022.
(Source: ResearchGate)
The proliferation of IoT devices, estimated to reach over 75 billion by 2025 according to a report by Statista, is not just a testament to human ingenuity but also a breeding ground for cybercriminals. This exponential growth, while facilitating unprecedented levels of convenience and efficiency, simultaneously broadens the attack surface, offering a multitude of vectors for exploitation.
The IoT security landscape is not only growing but diversifying. Cybercriminals are becoming more sophisticated, leveraging artificial intelligence and machine learning techniques to automate attacks on a scale previously unimaginable. Furthermore, the COVID-19 pandemic has accelerated the adoption of IoT devices in the healthcare sector, introducing new vulnerabilities at a time when the stakes for security breaches can be literally life-threatening.
Moreover, the integration of IoT devices in critical infrastructure sectors—such as energy, transportation, and water supply—presents a chilling vector for cyber-terrorist attacks that could disrupt the lives of millions.
The regulatory landscape is struggling to keep pace with these developments. While initiatives like the Internet of Things Cybersecurity Improvement Act of 2020 in the United States represent steps in the right direction, the global nature of the Internet and the diversity of IoT devices make it challenging to enforce comprehensive security standards.
In light of these challenges, the growing IoT threat landscape emphasizes the urgent need for a paradigm shift in how we approach IoT security. No longer can we afford to view security as an afterthought or a mere technical nuisance. It must be woven into the fabric of IoT innovation from the inception of each device.
Why Are IoT Devices Vulnerable?
IoT devices are inherently vulnerable due to several factors:
- Limited Computing Resources: Designed for specific functionalities, many IoT devices possess minimal computing power and storage, limiting their ability to host comprehensive security software.
- Insecure Default Settings: Devices shipped with default or hardcoded passwords are low-hanging fruits for attackers employing brute force methods.
- Lack of Encryption: A significant portion of IoT communication happens without encryption, exposing sensitive data to interception and manipulation.
- Component Uniformity: The use of common hardware components across multiple devices creates uniform vulnerabilities that can be exploited all together.
- Diverse Ecosystems: The IoT landscape is marked by a wide range of devices, operating systems, and protocols, complicating the implementation of standardized security measures.
- Insufficient Update Mechanisms: Many devices lack the capability for automatic updates, leaving known vulnerabilities unpatched.
- Underestimated Security Needs: Organizations often deploy IoT devices without fully understanding or addressing their security vulnerabilities.
- Complex Supply Chains: The IoT ecosystem involves a complex network of manufacturers, software developers, and service providers. Each entity in the supply chain might have different security standards and practices, creating inconsistencies in security protocols. This complexity not only complicates the implementation of uniform security measures but also introduces multiple points of vulnerability that attackers can exploit.
- Longevity and Lifecycle Concerns: IoT devices often have longer operational lifecycles compared to traditional computing devices. Security vulnerabilities discovered post-deployment can remain unaddressed due to the absence of mechanisms for patch management or updates, especially in devices deployed in hard-to-reach or critical infrastructure environments. This longevity turns them into dormant risks, potentially compromised without alerting stakeholders to the presence of an active threat.
- Insufficient Attention to End-of-Life Security: The end-of-life phase of IoT devices is often neglected from a security perspective. Disposal or decommissioning processes rarely include measures to securely erase data or ensure devices are not exploitable post-deactivation. This oversight can lead to scenarios where discarded devices, still containing sensitive data or exploitable software, become sources for data breaches or cyber-attacks.
The Spectrum of IoT Malware and Attacks
IoT malware exploits the vulnerabilities inherent in connected devices to carry out various malicious activities:
- IoT Botnets: These are networks of compromised devices used to launch distributed denial-of-service (DDoS) attacks, overwhelming targets with traffic.
- Ransomware: Malicious software that encrypts data or locks users out of their devices, demanding ransom for restoration.
- Destruction ware: Malware aimed at causing physical damage or disrupting services, often with political or ideological motives.
- Rogue Devices: Unauthorized devices added to a network can facilitate further breaches or serve as gateways for attacks.
- Advanced Persistent Threats (APTs) in IoT: APTs represent a significant threat to IoT environments, involving stealthy and continuous computer hacking processes to gain access to a system and remain undetected for an extended period. IoT devices, with their always-on connectivity and access to vast networks, provide an ideal platform for attackers to establish footholds within networks, from where they can conduct espionage, data exfiltration, or long-term damage.
- Cross-Site Scripting (XSS) and SQL Injection via IoT: With IoT devices increasingly interacting with web applications and databases, vulnerabilities like XSS and SQL Injection can be exploited to execute malicious scripts or manipulate database queries. These attacks can lead to unauthorized access to sensitive information, data breaches, and further network infiltration.
- Zero-Day Exploits: IoT ecosystems are particularly vulnerable to zero-day exploits, where attackers take advantage of previously unknown vulnerabilities before developers have had a chance to issue fixes. The diversity and fragmentation of the IoT landscape, combined with the slow pace of updates and patches, make managing these threats especially challenging.
- Man-in-the-Middle (MitM) Attacks: Insecure data transmission and lack of encryption in many IoT devices allow attackers to intercept communications between devices and servers. Through MitM attacks, cybercriminals can steal or manipulate data, disrupt services, or impersonate devices to gain unauthorized access to networks.
- Supply Chain Attacks: Given the complex supply chains involved in the development and distribution of IoT devices, attackers are increasingly targeting less-secure elements in the supply chain to compromise devices before they even reach consumers. These attacks can result in pre-installed malware or vulnerabilities that threaten the entire lifecycle of the device.
Fortifying IoT Security: Best Practices and Strategies
Protecting IoT devices from malware requires a multi-faceted approach, combining proactive strategies with robust security measures:
Enhancing Device Security:
- Strengthen Authentication: Implement strong, unique passwords and consider multi-factor authentication to secure access points.
- Employ Encryption: Use encryption for data at rest and in transit to protect against unauthorized access and data breaches.
- Minimize Attack Surfaces: Disable unnecessary features and services on devices to reduce potential vulnerabilities.
- Regular Updates and Patch Management: Establish a routine for updating device firmware and software to address security vulnerabilities promptly.
Network and Communication Security:
- Network Segmentation: Isolate IoT devices on separate network segments to limit the spread of potential attacks and ease network management.
- Secure APIs: Ensure APIs, which facilitate communication between IoT devices and backend systems, are secure and accessible only to authorized entities.
- Asset Inventory and Management: Maintain an up-to-date inventory of all IoT devices to monitor for unauthorized devices and manage security policies effectively.
Proactive Defense and Detection:
- Advanced Monitoring and Anomaly Detection: Deploy advanced monitoring tools and techniques to detect unusual activities and potential threats in real-time.
- Embrace AI and Machine Learning: Utilize artificial intelligence and machine learning for dynamic threat analysis and predictive security measures.
- Implement Strong EDR/XDR Solutions: Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR) solution provides comprehensive visibility and rapid response capabilities across the IoT ecosystem.
Organizational and User Awareness:
- Security Awareness Training: Educate staff and users on the importance of IoT security and best practices to mitigate risks.
- Remote Work and IoT: Develop and enforce policies for securely integrating consumer IoT devices within corporate networks, especially in remote work scenarios.
- Community Engagement and Collaboration: Participate in industry forums, share threat intelligence, and collaborate on developing best practices for IoT security.
Looking Forward: The Future of IoT Security
As the IoT landscape continues to expand, the imperative for robust security measures becomes increasingly critical. The future of IoT security lies in the development of advanced, adaptive security technologies and frameworks capable of combating evolving IoT threats. Partnering with a trusted
IoT security solutions provider will play a pivotal role in establishing a powerful line of defense.
The integration of IoT devices into our daily lives and industrial processes offers immense benefits but also introduces significant security challenges. By understanding the vulnerabilities, implementing robust security measures, and adopting a proactive defense strategy, organizations can protect their IoT ecosystems from malware and cyber threats. As we navigate this interconnected world, the collective efforts of technology providers, cybersecurity experts, and regulatory bodies will be crucial in shaping a secure digital future.
Reach out to our IoT security expert to learn more about our cutting-edge IoT security solutions and expertise.
