Industrial IoT under Siege: Navigating Threats and Vulnerabilities

Futurism Technologies
October 6, 2023 - 3.2K
5 Min Read
In the age of digitization, where the virtual and physical worlds intertwine, the rapid adoption of the Industrial Internet of Things (IIoT) promises unparalleled efficiency, connectivity and innovation. However, with increased connectivity comes heightened susceptibility to cyber threats. As the IIoT ecosystem expands, so does the ambit of cyber-threat actors who will increasingly try to exploit these advanced and connected systems.
Read also: The Rise of Backdoor Attacks – New Cyber Nightmare!
Cyber Threats: The New Reality for Industrial IoT
The allure of IIoT for cyber attackers is clear: an interconnected landscape that manages critical infrastructures like power grids, water supply chains, and manufacturing units. A successful breach can lead to catastrophic consequences.
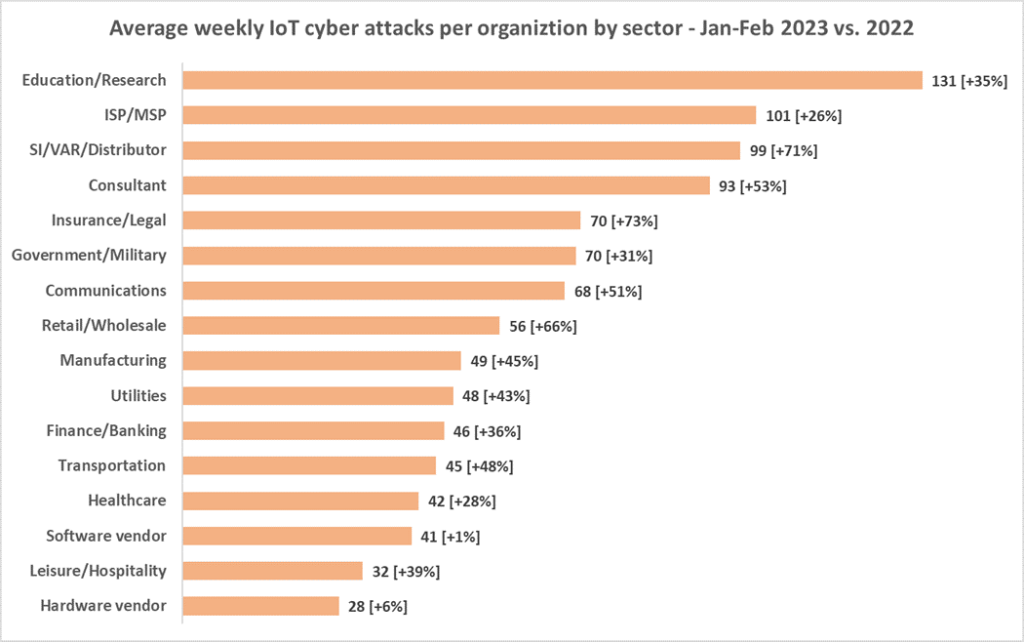
According to the Cybersecurity and Infrastructure Security Agency (CISA), incidents targeting IIoT systems have seen a sharp rise in the last couple of years. In fact, a recent report suggests that nearly 70% of industries have witnessed an IIoT-related security incident in the past year.
A typical attack might commence with a phishing email to an unsuspecting employee. Once inside the network, attackers move laterally, seeking vulnerabilities in IIoT systems. Often, the aim is to gain control, disrupt operations, or hold the system for ransom. One notable example is the 2020 attack on a water treatment facility in Florida, where hackers manipulated IIoT systems to alter the chemical balance of the water.
Read also: Major Engineering Giant Hit with Ransomware!
Safeguarding Industrial Assets: Best Practices
Securing IIoT doesn’t merely entail the latest firewall or antivirus software. It requires a holistic cybersecurity awareness and approach.
- Network Segmentation: Separate IIoT devices from regular IT networks to contain potential breaches. This isolation can prevent a breach from propagating across the entire system.
- Regular Audits and Patching: Outdated software is a magnet for cyberattacks. A regular audit of IIoT devices, followed by timely patching of identified vulnerabilities, can significantly reduce exposure. Conducting vulnerability assessment and penetration testing on a regular basis can go a long way in preventing such IoT cyberattacks.
- Employee Training: Human error remains a significant vulnerability. Regular training can equip employees to recognize and resist common attack vectors like phishing.
- Multi-factor Authentication (MFA): Implement MFA for all IIoT device access. This additional layer can deter unauthorized access attempts.
- Collaborate with Vendors: Work closely with IIoT device manufacturers. They often provide updates and guidance on recognized vulnerabilities.
Read also: Hackers Pose as Cybersecurity Firm to Trick Victims in a New Social Engineering Hack Tactic
The Regulatory Landscape: Rising to the Challenge
Companies must remain vigilant about understanding and complying with the necessary security compliances and regulations, not only to avoid penalties but more critically, to ensure the security and safety of their operations and the larger community.
Harnessing Futurism’s Endpoint Secure for Industrial IoT Protection
In an increasingly complex digital landscape where IIoT vulnerabilities are targeted, a robust defense mechanism is not just preferred but essential. Addressing these concerns head-on, Futurism Technologies offers its cutting-edge IoT security solution – Endpoint Secure.
The Futurism EndPoint Secure Advantage:
- Holistic Protection: Futurism’s Endpoint Secure is designed with a comprehensive approach. It doesn’t just aim to detect threats but actively prevents them, ensuring that IIoT systems remain safe from malicious actors.
- Real-time Monitoring: With the rapid pace of cyberattacks, real-time vigilance is imperative. Endpoint Secure offers 24/7 monitoring, ensuring threats are identified and neutralized in their infancy, long before they escalate into full-blown breaches.
- Integrated AI: In the age of smart cyber-attacks, smart defenses are crucial. By harnessing AI-powered threat intelligence, Endpoint Secure stays ahead of emerging threats, learning continuously from the global threat landscape to fortify defenses.
- Customized for IIoT: Recognizing that IIoT has distinct needs, Futurism has ensured that Endpoint Secure is tailored for industrial environments. This fine-tuning ensures that while threats are kept at bay, operational efficiency remains unhindered.
- Seamless Updates: The ever-evolving nature of cyber threats necessitates that protective solutions remain up-to-date. Futurism’s proactive approach ensures that Endpoint Secure is always equipped with the latest patches and defenses.
Goes beyond just endpoints, Futurism EndPoint Secure is a specialized IoT security solution designed to bolster the security fabric of interconnected devices. Backed by AI-powered threat intelligence and technology, EndPoint Secure ensures that the interconnectedness that IIoT thrives on does not become a breeding ground for threat actors and cybercriminals.
Takeaway
In today’s world, where cyber threats to IIoT are not just hypothetical but a pressing reality, solutions like Endpoint Secure by Futurism Technologies stand as the vanguard of defense. By adopting such advanced protective measures, industries can focus on harnessing the immense potential of IIoT, secure in the knowledge that their operations are safeguarded against malicious actors.
The advancement of IIoT brings forth opportunities and challenges in equal measure. As industries harness its untapped power, understanding the lurking threats and adopting best practices is non-negotiable. Moreover, as the regulatory sands shift, keeping an ear to the ground and a proactive approach will ensure that industries don’t just survive but thrive in this connected era.
To delve deeper into how Endpoint Secure can fortify your connected IIoT infrastructure, contact us now to book a FREE demo.
Subscribe Now!
TRENDING POSTS
-
Futurism Returns to Hannover Messe 2024: Leading the Charge in Industrial and Digital Transformation
-
The Role of Smart Maritime IoT Solutions in Enhancing Maritime Safety
-
Data Integration Unlocked: From Silos to Strategy for Competitive Success
-
Navigating the Shadows: Understanding Zero-Click Attacks in the Digital Age
-
AI Reimagined: Crafting Next-Gen AI Apps with Expert Fine-Tuning
-
Explore Next-Gen Digital Solutions with Futurism at MWC 2024
-
Futurism Unleashes the Technology of Tomorrow at MWC Barcelona 2024
-
Futurism AI: Turning Ideas into Apps at Lightning-Fast Speed
-
Accelerate AI Across Your Enterprise With Futurism AI
-
Futurism to Address the Biggest Security Challenges at RSS 2022
-
Futurism at SelectUSA 2022: Steering the Next Wave of Businesses
-
Futurism to Uplift the MSP Business Community at the MSP Expo 2022
-
Futurism Sets Out to Address the Biggest Security Challenges at the RSA Conference 2022
-
5 Ways to Prepare Your Business for Digital Transformation
-
4 Ways To Win at Digital Transformation on a Shoestring Budget
-
Futurism: Empowering MSPs at the Channel Partners Conference & Expo 2022
-
Why AI in Digital Marketing is the Next Big Thing?
-
Futurism brings ‘Mobile First Digital Transformation’ to the fore at MWC Barcelona 2022
-
Cybersecurity for Rural Hospitals: How can Rural Hospitals become Cyber Smart?
-
Futurism Empowers Rural Health Care Community at the AHA Rural Health Care Leadership Conference
-
The Biggest Problem With Cybersecurity In Healthcare Sector, And How IBM QRadar Can Fix It?
-
How IBM MaaS360 is Revolutionizing Endpoint Security in the Healthcare Industry?
-
Futurism to Present its MSP Partner Program at the Channel Partners Conference & Expo 2021
-
EndPoint Security in Healthcare Matters and IBM MaaS360 Can Help
-
How AI Will Enable Faster Adaptation of Digital Transformation
-
How Is Digital Modernization Important In Supplier On-Boarding?
-
Top 10 Email Marketing Tips for This Holiday Season
-
Benefits of using ERP Software for Energy and Gas Industries