EndPoint Security in Healthcare Matters and IBM MaaS360 Can Help

Futurism Technologies
August 30, 2021 - 6.2K
5 Min Read
Faced with a streak of sophisticated and next-level cyber attacks, healthcare industry has found itself at the center of a perfect cyber storm.
FBI has issued a serious warning of ‘imminent’ cyber attacks on hospitals in USA and all over the world in 2021 and beyond. Healthcare organizations particularly in the U.S. are at greater risk of cybersecurity incidents that are expected to complicate their operations and hurt their profits, according to IBM.
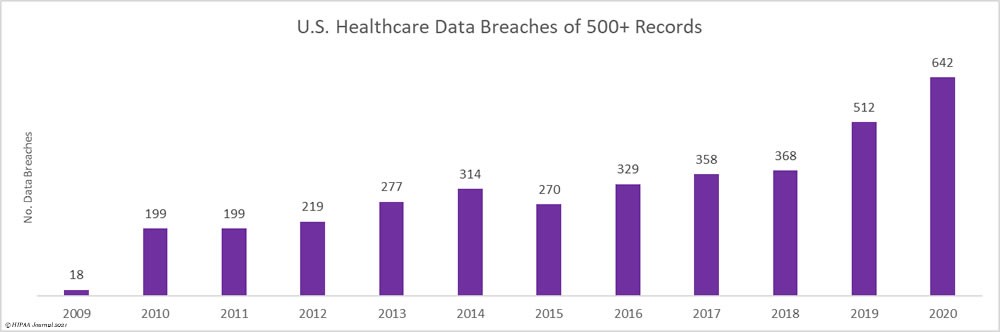
(Source: HIPAA Journal)
Cybercriminals and hackers have been continually targeting hospitals and healthcare institutions to steal sensitive patient information. In fact, attacks on healthcare IoT and mobile devices have tripled since the onset of the COVID-19 pandemic. Yes, COVID-driven cyber incidents saw a streak of Ransomware, social engineering and multi-prong attacks against healthcare organizations in 2020.
An increasing number of healthcare organizations are finding themselves in troubled waters when it comes to securing patient information and medical records in today’s digital-first era. This is because most hospitals and healthcare providers still stuck in the ice age rely on traditional cybersecurity and poor IT/security hygiene practices and lack certified cybersecurity personnel at their disposal to deal with evolving cyber threats.
Did you know?
According to NSA and FBI, healthcare records continue to be the hot targets for multi-prong cyber attacks!
What hospitals need to know?
2020 unleashed a perfect storm for attackers with Ransomware attacks costing the healthcare industry a whopping $21 billion. (Source: Comparitech)

Today, healthcare organizations churn out more data than ever, which is shared throughout the healthcare supply chain. However, loosely secured networks and endpoints operated and accessed by healthcare organizations increase security challenges to a great extent.
Even medical equipment and devices such as heart monitors, electrocardiogram and MRI machines, blood pressure monitors, implanted defibrillators, IV pumps, etc. collect and store sensitive patient data on daily basis and thus, provide an avenue for cybercriminals and hackers to access databases in a healthcare organization’s system.
These are just a handful number of endpoints on the network of most healthcare organizations today. Hackers can freeze hospital devices and systems affecting treatment times, care delivery thus, putting lives at danger. No hospital can afford to lose access to patient data at any cost and avoiding downtime is critical.
Unfortunately, the healthcare industry despite being the hot target among cyber criminals has been slow when it comes to using encryption for internal operations, often citing cost and productivity reasons. Attackers today are well aware of the fact that cyber budgets are super low and most hospitals run on outdated technology that’s difficult to secure thus, making them soft targets. Healthcare systems appear as low-hanging fruits for attackers and cyber criminals. Moreover, with the wide adoption of digital front door concept among healthcare organizations and care providers, hospitals today are super connected than before making hack easier than ever.
As the inventory and the network of mobile and connected medical devices continue to grow, IT admins and security professionals face two key challenges i.e. optimizing access to these lifesaving devices and protecting their critical data from cybercriminals. According to a Verizon study, more than 20% of healthcare organizations have experienced a security breach involving mobile devices in the past 12 months.
IT and security folks at healthcare organizations ought to identify every type of data that requires protection. These can be anything from port and access restrictions to strong encryption methods and tokenized data vaults to selective network segregation and identify management. The goal is to prevent suspicious or unauthorized breach attempts and secure endpoints.
These security concerns are prompting security and IT leaders to embrace a robust and wide-ranging approach to endpoint management to prevent hacking and achieve maximum visibility and control of their networks.
Hospitals Need to Ramp up EndPoint Security Management

Healthcare organizations including pharmaceutical companies and biotech firms are entrusted to protect sensitive data such as HIPAA-protected info, proprietary drug research info, financial data, etc. at all cost. This also include patient data that often appears appealing to cybercriminals looking to get access to sensitive information to sell or extort. Someone with unrestricted access to such sensitive data or files can copy, delete or change tons of documents endangering lives and incurring massive losses to a hospital.
Hackers are very much inclined to install a Ransomware on a healthcare system, which locks down or freezes the entire system until the ransom is paid. Also, there are phishing attacks that can occur by employees of a hospital accidentally believing that a malicious email content is safe to click or download.
Endpoints are high-risk doorways on a hospital’s network. In addition, they are the point of contact with the users, who unfortunately are the weakest link in any security strategy. Further, the complex network of connected medical and IoT devices make it extremely challenging for security and IT admins to deal with threats and attacks in real-time.
According to Tenable, more than 20 billion health records including sensitive patient data were exposed in 2020.
Mobile and connected medical devices present a grave insidious threat to any hospital, since an intrusion or virus could hurt or even kill a patient as a result of how the attacker impacts the device. Further, a constant influx of contractors, physicians, visitors and patients into the system poses a major challenge. Security admins ought to monitor these connections and traffic to look out for troubled or suspicious sign-in attempts, large-scale data exfiltration, etc.
Several security measures can work when it comes to defense. For instance, two-factor authentication, scanning for open access points, access logging, encryption, etc. could help curb risks along with strong device policies that require device authorization on a personal level.
Managed endpoint security solutions are making great inroads in healthcare landscape and IBM is a clear winner. Yes, IBM MaaS360 has been a hot-pick among hospitals and healthcare organizations around the world when it comes to security infrastructure and endpoint management.
Hiring the services of a trusted managed endpoint security service provider, hospitals and healthcare leaders can ramp up employee awareness, patch or encrypt all software, enforce enhanced endpoint security and threat protection policies and get better visibility and control over all their critical endpoints and digital front doors.
Developed with IBM, Futurism EndPoint Secure helps you leverage the power of IBM MaaS360in a cost-efficient manner. EndPoint Secure is a managed MDM security service designed to suit hospitals of all sizes and to help them get the most out of IBM Security.
Offered as a fully managed security service, EndPoint Secure helps to manage endpoint policies and security threats for all your critical endpoints including mobile phones, desktops, wearables, tablets, and connected healthcare IoT devices to deliver better visibility and control over your data and devices.
Explore the power of IBM MaaS360 with Futurism EndPoint Secure:
- Mobile Device Management (MDM Services)
- AI-driven Threat intelligence (powered by IBM Watson & X-Force)
- Fully-encrypted container to protect app and device data
- Mobile security index
- Unified Endpoint Management (UEM)
- Identity and access management (IAM) & Mobile application management (MAM)
- Device location tracking & remote security controls
- Multiple devices and OS support (iOS, Android, Microsoft Windows devices and tablets, etc.)
- 24/7 Security Operations Centre monitoring
- Cloud Identity Access Management
- Real-time Reporting and Analytics
- Centralized management of all your Endpoints
Check out this cool video to experience IBM MaaS360
We can help you deploy a robust asset monitoring and discovery strategy in place for your hospital in order to gain better visibility into the fast-expanding attack surface, which includes cloud apps, connected devices, IoT systems, etc.
Healthcare organizations lack the necessary skills or resources to counter these attacks. For such organizations, it is high time that they ask for help and engage a trusted managed security service provider (MSSP) that boasts of top-notch security expertise and track record. With an MSSP, healthcare organizations don’t have to purchase expensive security products neither do they have to hire additional security skills, which are difficult to find and retain.
To learn how Futurism can help you harness the power of IBM MaaS360 for your hospital, get in touch with one of our security experts at +1 (732) 790-2593 or book a FREE consultation here.
Subscribe Now!
TRENDING POSTS
-
Futurism Returns to Hannover Messe 2024: Leading the Charge in Industrial and Digital Transformation
-
The Role of Smart Maritime IoT Solutions in Enhancing Maritime Safety
-
Data Integration Unlocked: From Silos to Strategy for Competitive Success
-
Navigating the Shadows: Understanding Zero-Click Attacks in the Digital Age
-
AI Reimagined: Crafting Next-Gen AI Apps with Expert Fine-Tuning
-
Explore Next-Gen Digital Solutions with Futurism at MWC 2024
-
Futurism Unleashes the Technology of Tomorrow at MWC Barcelona 2024
-
Futurism AI: Turning Ideas into Apps at Lightning-Fast Speed
-
Accelerate AI Across Your Enterprise With Futurism AI
-
Futurism to Address the Biggest Security Challenges at RSS 2022
-
Futurism at SelectUSA 2022: Steering the Next Wave of Businesses
-
Futurism to Uplift the MSP Business Community at the MSP Expo 2022
-
Futurism Sets Out to Address the Biggest Security Challenges at the RSA Conference 2022
-
5 Ways to Prepare Your Business for Digital Transformation
-
4 Ways To Win at Digital Transformation on a Shoestring Budget
-
Futurism: Empowering MSPs at the Channel Partners Conference & Expo 2022
-
Why AI in Digital Marketing is the Next Big Thing?
-
Futurism brings ‘Mobile First Digital Transformation’ to the fore at MWC Barcelona 2022
-
Cybersecurity for Rural Hospitals: How can Rural Hospitals become Cyber Smart?
-
Futurism Empowers Rural Health Care Community at the AHA Rural Health Care Leadership Conference
-
The Biggest Problem With Cybersecurity In Healthcare Sector, And How IBM QRadar Can Fix It?
-
How IBM MaaS360 is Revolutionizing Endpoint Security in the Healthcare Industry?
-
Futurism to Present its MSP Partner Program at the Channel Partners Conference & Expo 2021
-
EndPoint Security in Healthcare Matters and IBM MaaS360 Can Help
-
How AI Will Enable Faster Adaptation of Digital Transformation
-
How Is Digital Modernization Important In Supplier On-Boarding?
-
Top 10 Email Marketing Tips for This Holiday Season
-
Benefits of using ERP Software for Energy and Gas Industries


