How CTEM Helps CISOs Slash Cyberattacks by 60%

Futurism Technologies
September 16, 2025 - 1.2K
5 Min Read
In today’s digital battlefield, waiting for the next cyberattack is not an option continuous threat exposure management (CTEM) is your frontline defense.
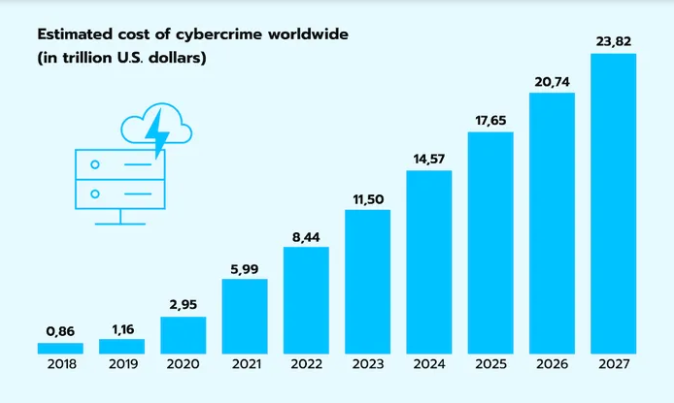
Cyberattacks are occurring more often, with increased complexity and greater potential damage than ever seen before. Cybersecurity Ventures projects that the global cost of cybercrime will rise dramatically, reaching $10.5 trillion per year by 2025, up from $3 trillion in 2015. For Chief Information Security Officers (CISOs) leading security in organizations, this growing threat landscape presents an urgent challenge: how to stay ahead and protect your business in real-time.
Traditional cybersecurity methods like periodic vulnerability scans and reactive patching are no longer enough. Cybercriminals exploit blind spots between these assessments, leaving organizations exposed. This is where Continuous Threat Exposure Management (CTEM) comes into play a game-changing approach that provides CISOs with ongoing visibility and control over their security posture.
In this blog, we’ll dive deep into why CTEM is the winning bet for CISOs in 2025, how it works, the benefits it offers, and practical steps to implement it in your organization.
What is CTEM and Why Does It Matter?
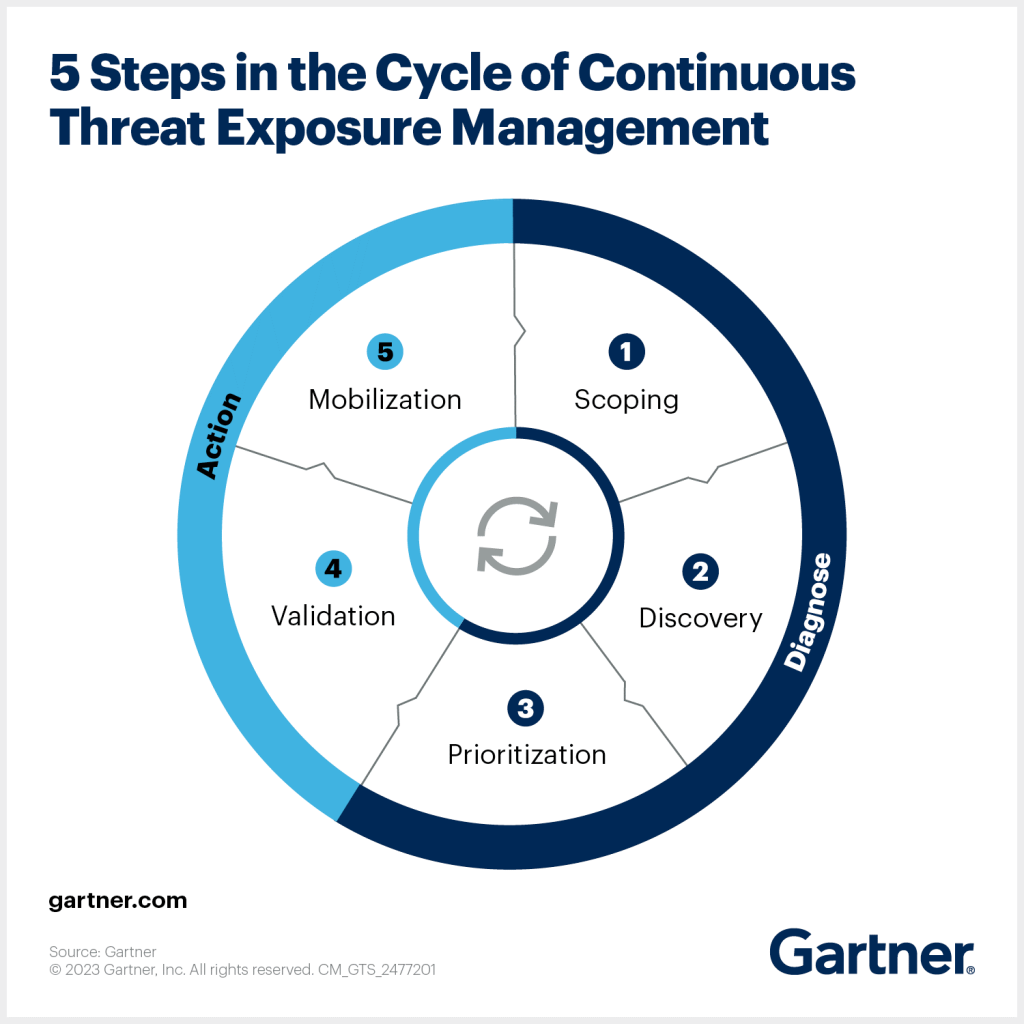
At its core, Continuous Threat Exposure Management (CTEM) is a proactive cybersecurity strategy that continuously identifies, prioritizes, and manages an organization’s exposure to threats. Unlike traditional vulnerability management which typically provides a snapshot of security at a point in time CTEM delivers ongoing, real-time insights into your entire attack surface.
How CTEM works:
- Simulates attacker behavior to identify how vulnerabilities can be exploited.
- Continuously scans across on-premises, cloud, and remote assets.
- Prioritizes exposures based on risk to the business.
- Provides actionable remediation guidance.
This continuous, real-world approach helps CISOs understand where their biggest risks lie, making it easier to allocate resources effectively and prevent attacks before they happen.
To dive deeper into how cutting-edge technologies like AI are reshaping cybersecurity strategies including CTEM check out our comprehensive guide:
AI and Cybersecurity: A Futurism Guide.
The Top Cybersecurity Challenges CISOs Face Today
Managing cybersecurity today is like trying to hit a moving target. CISOs commonly face several major challenges, including:
- Expanding Attack Surfaces: With remote work, cloud adoption, IoT devices, and third-party vendors, organizations’ digital footprints have exploded. Market expert reports that by 2025, 75% of cyberattacks will target non-traditional IT assets like cloud workloads and IoT devices.
Also Read – 10 Ways to Secure your Remote Workforce
- Siloed Security Tools: Many organizations use multiple security solutions that don’t communicate well, creating gaps and blind spots.
- Reactive Posture: Traditional methods rely heavily on scheduled scans and patches, leaving time windows where attackers can slip through.
- Prioritization Difficulties: CISOs often struggle to determine which vulnerabilities pose the greatest risk, leading to inefficient use of limited resources.
These challenges demand a new approach one that provides continuous, real-time visibility and helps CISOs focus on what truly matters.
How CTEM Solves These Challenges Head-On
Continuous Threat Exposure Management offers a holistic and dynamic solution to modern cybersecurity woes:
1. Complete, Real-Time Visibility
CTEM continuously scans your entire attack surface, from cloud infrastructure to remote endpoints, ensuring no asset is overlooked. This helps you detect exposures immediately instead of waiting for periodic scans.
2. Attack Simulation for Realistic Insights
By simulating attacker behavior and potential attack paths, CTEM goes beyond just listing vulnerabilities. It provides clear insights into real risks and how likely they are to be exploited, allowing you to concentrate on the most critical issues.
3. Prioritized, Risk-Based Remediation
CTEM ranks exposures by their potential business impact, allowing your security teams to prioritize efforts effectively. No more guessing which vulnerabilities to patch first.
4. Data-Driven Decision Making
Dashboards and reports provide CISOs with actionable intelligence to communicate security posture to stakeholders and guide strategic investments.
5. Integration with Existing Security Ecosystems
CTEM platforms integrate with your current tools like SIEM, SOAR, and vulnerability scanners, enhancing your overall security architecture without disruption.
Benefits of Adopting CTEM
Here’s why CTEM is becoming the go-to approach for CISOs across the USA:
- Proactive Risk Reduction: Instead of reacting after a breach, CTEM helps prevent incidents by continuously identifying and addressing exposures.
- Improved Compliance and Reporting: Many regulations now require ongoing risk management. CTEM simplifies compliance by offering continuous evidence of risk posture.
- Better Resource Allocation: Prioritization means your security budget goes to the highest-impact issues, improving cost efficiency.
- Quicker Incident Response: Real-time monitoring enables your teams to identify and address threats more promptly.
- Supports Digital Transformation: As organizations move to cloud and hybrid environments, CTEM provides the adaptive security needed to keep pace.
According to Market Research, organizations using continuous risk monitoring and exposure management solutions reduce their breach impact by up to 60%. That’s a game-changer in today’s threat environment.
How to Implement CTEM: Best Practices for CISOs
If you’re ready to adopt CTEM, here are practical steps to ensure success:
1. Evaluate and Choose the Right CTEM Platform
Look for platforms offering comprehensive asset discovery, attack simulation, risk prioritization, and seamless integration with your existing security tools.
2. Align with Your Security Policies
Ensure CTEM fits within your organization’s risk appetite, compliance requirements, and cybersecurity strategy.
3. Train Your Security Teams
Empower your teams with training on how to interpret CTEM insights and translate them into effective remediation actions.
4. Establish Continuous Monitoring and Reporting
Set up automated dashboards and regular reports for real-time tracking of exposure status and progress.
5. Use CTEM Insights for Executive Communication
Leverage CTEM data to provide transparent, quantifiable risk reporting to your board and stakeholders.
Why CTEM Will Remain Vital in Cybersecurity’s Future
Cyber threats are evolving rapidly, driven by increased connectivity, automation, and AI-powered attacks. Market experts predicts that by 2027, 90% of organizations will use exposure management platforms to reduce cyber risk.
CTEM’s continuous, adaptive nature makes it an essential pillar of resilient cybersecurity frameworks. Integration with AI and machine learning will only enhance its capabilities, enabling smarter threat prediction and response.
Implementing CTEM today equips CISOs to help their organizations not only withstand but excel in the face of upcoming cybersecurity threats.
Conclusion:
The cybersecurity landscape demands constant vigilance and adaptability. Continuous Threat Exposure Management provides CISOs with real-time awareness, prioritized risks, and practical insights to outpace cyber threats. It’s no longer enough to patch after the fact proactive exposure management is the future.
If you’re a CISO looking to strengthen your security posture, reduce risks and optimize your resources, CTEM is your winning bet for 2025.
Ready to explore how CTEM can transform your cybersecurity strategy? Contact Futurism Technologies today to learn more about our advanced threat exposure management solutions.
Subscribe Now!
TRENDING POSTS
-
Agentic AI and Generative AI: What’s Best for Your Business?
-
Deepfake Scams: How to Protect Your Business in the Age of AI
-
AI and Cybersecurity: A Strategic Guide for C-Suite Leaders in 2025
-
How Location Intelligence is Revolutionizing BFSI: 6 Must-Know Benefits
-
Cloud and Data Engineering: The Path to Faster Insights and Smarter Decisions
-
From Delays to Innovation: How AI is Optimizing the Construction Industry
-
Data-Driven Future: 6 Trends to Watch Out For
-
The Impact of IoT on Reducing Maritime Carbon Footprints
-
Demystifying SASE: What is Secure Access Service Edge?
-
The Role of AI in Construction Safety
-
What Is Predictive Maintenance and Why Does It Matter?
-
What is Ransomware-as-a-Service (RaaS)? Everything You Need To Know
-
The Role of Smart Maritime IoT Solutions in Enhancing Maritime Safety
-
Revolutionizing Telecom with AI-Driven Network Slicing
-
Data Integration Unlocked: From Silos to Strategy for Competitive Success
-
Navigating the Shadows: Understanding Zero-Click Attacks in the Digital Age
-
AI Reimagined: Crafting Next-Gen AI Apps with Expert Fine-Tuning
-
Futurism AI: Turning Ideas into Apps at Lightning-Fast Speed
-
Accelerate AI Across Your Enterprise With Futurism AI
-
Flying into the Future: How AI is Redefining the Future of Aviation
-
Beyond Intelligence: The Rise of Self-Healing AI
-
The Indispensable Role of a Trusted Offshore AI Company in 2024 & Beyond
-
IoT-Powered Smart Warehouse Management: A Detailed Guide
-
Turning Data into Dollars: The Futurism Path to AI-Driven Success
-
5 Ways to Prepare Your Business for Digital Transformation
-
4 Ways To Win at Digital Transformation on a Shoestring Budget
-
Why AI in Digital Marketing is the Next Big Thing?
-
How AI Will Enable Faster Adaptation of Digital Transformation
-
How Is Digital Modernization Important In Supplier On-Boarding?
-
Top 10 Email Marketing Tips for This Holiday Season
-
Benefits of using ERP Software for Energy and Gas Industries
-
5 Features of Supply Chain Management Software





