What is Ransomware-as-a-Service (RaaS)? Everything You Need To Know

Futurism Technologies
May 2, 2024 - 5.2K
5 Min Read
In an age where technology intertwines with every facet of our lives, the sword of innovation cuts both ways. On one hand, advancements in digital technology have propelled us into an era of unparalleled convenience and connectivity. Yet, on the flip side, this progress has opened Pandora’s box of cyber threats. Among these threats lurks a particularly insidious menace: Ransomware-as-a-Service aka RaaS.
Imagine a world where cybercrime is commoditized, where the tools for digital extortion are available off-the-shelf for anyone with malicious intent and a bit of cryptocurrency. This is not a dystopian future; it is a present reality. As we stand on the brink of this digital cliff, it’s imperative to understand the forces at play.

(Source: VentureBeat)
Futurism Technologies steps into this arena, not just as a spectator but as a guardian of the digital realm. Our journey into the heart of RaaS is more than an exploration; it’s a call to arms, inviting you to join us in fortifying the digital future against this looming threat. Let’s peel the layers of RaaS together, unraveling its complexities and demystifying its operations, for knowledge is our most potent weapon in this unseen war.
Understanding the Evolution of Ransomware-as-a-Service (RaaS)
Ransomware, in its traditional form, is some type of malicious software that encrypts a victim’s data and demands some ransom amount to provide the decryption key or a way out of it to retrieve the data back. Ransomware attacks have been like a plague on the digital landscape for many years, with both – individuals and organizations, falling prey to the disruptive and costly consequences. However, the RaaS represents a noticeable shift and progress in the world of cybercrime.
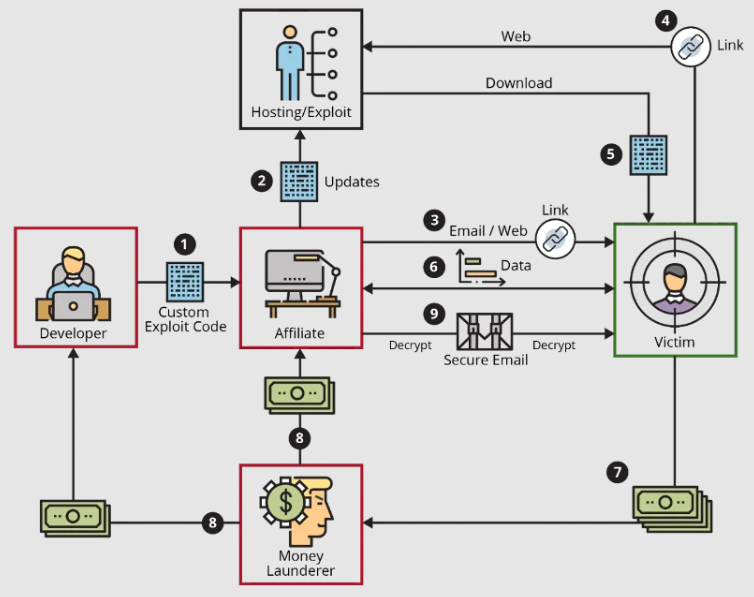
RaaS providers are essentially cybercriminals-for-hire who offer ransomware tools, infrastructure, and support to other criminals, often for a share of the ransom profits. This model has democratized cybercrime, making it more accessible to a broader range of attackers. It provides them with a turnkey solution, including customizable ransomware variants and a distribution network, enabling them to launch attacks with minimal technical expertise.
Read also: The Anatomy of a Ransomware Attack: How Does Ransomware Work?
Inside the RaaS Ecosystem
The RaaS ecosystem is a complex network of cyber criminals, with different roles and responsibilities. It typically comprises of the following:
- Ransomware Developers: These are individuals or groups responsible for creating the ransomware. They design the malicious code, develop the encryption algorithms, and ensure the ransomware can effectively evade security measures.
- Affiliates: These are the users of RaaS who distribute the ransomware. They may be independent operators or part of a larger cybercriminal organization. Affiliates are responsible for spreading the malware to potential victims.
- Ransom Negotiators: In some RaaS operations, there are individuals who engage in negotiations with victims, facilitating the payment of ransoms in exchange for decryption keys.
- Service Providers: These entities offer infrastructure and support to the RaaS operators. This includes hosting ransomware servers, providing communication channels, and ensuring that payments are processed.
- Brokerage Platforms and Customer Support: A crucial, yet often overlooked, facet of the RaaS ecosystem is the emergence of brokerage platforms. These platforms act as intermediaries between ransomware developers and affiliates, streamlining the distribution and operation of ransomware campaigns. They provide a marketplace where affiliates can pick and choose from various ransomware products, much like selecting software on an app store.
- Cryptocurrency Integration and Anonymity Services: The financial backbone of the RaaS ecosystem relies heavily on cryptocurrencies, with Bitcoin being the most commonly used due to its widespread acceptance. However, to enhance anonymity and reduce traceability, RaaS operations are increasingly incorporating privacy-focused cryptocurrencies.
As the RaaS model continues to mature, a trend towards specialization and segmentation within the ecosystem is becoming more apparent. This evolution mirrors traditional business structures, where specialization leads to improved efficiency and outcomes. Within the RaaS ecosystem, specific groups or individuals focus on particular aspects of the ransomware lifecycle, such as initial access brokerage, where cybercriminals specialize in breaching and selling access to compromised systems.
Why is Ransomware-as-a-Service a Lethal Cyber Threat?
Ransomware-as-a-Service poses a significant threat to businesses and individuals for several reasons:
- Low Barrier to Entry: RaaS lowers the entry bar for aspiring cybercriminals. They no longer need to have any advanced technical skills to perform a ransomware attack, as they can simply purchase the tools and support that they need to complete their task.
- Evolving Variants: RaaS providers progressively develop new variants of ransomware, making it challenging for any traditional security measures to keep up with it. This adaptability increases the success rate of attacks.
- Wide Attack Surface: The vast network of affiliates means that RaaS attacks can target a wide range of industries, individuals, and geographical regions. No one is immune and is difficult to escape from it!
- Monetary Incentive: Ransomware attacks is a moneymaking way for cybercriminals. RaaS operators often take a percentage of the ransom, creating a financial incentive for the growth of this industry.
- Sophisticated Tactics: RaaS providers are known to employ advanced tactics, such as double extortion, where they not only encrypt data but also steal sensitive information to increase pressure on victims to pay.
- Anonymity and Payment Evasion: RaaS operations heavily rely on cryptocurrencies for ransom transactions, offering a high degree of anonymity to the attackers. This use of digital currencies complicates efforts by law enforcement and cybersecurity teams to trace and apprehend the culprits, allowing them to operate with relative impunity.
- Automated Attack Platforms: Some RaaS offerings have evolved into sophisticated automated platforms that enable attackers to customize and launch attacks with minimal effort. These platforms can scale malicious activities, allowing for simultaneous attacks on multiple targets, which increases the overall effectiveness and reach of ransomware campaigns. This automation also lowers the cost and complexity of launching attacks, attracting more participants to the RaaS ecosystem.
- Exploitation of Zero-Day Vulnerabilities: RaaS developers often invest resources in discovering or purchasing zero-day vulnerabilities, which are flaws in software that are unknown to the vendor. These vulnerabilities are particularly valuable because they can be exploited to breach systems before a patch is available. By leveraging zero-day vulnerabilities, RaaS attacks can bypass conventional security measures, making them significantly harder to prevent and detect.
- Supply Chain Attacks: RaaS operators are increasingly targeting managed service providers (MSPs) and software vendors in supply chain attacks. By compromising a single MSP or software update mechanism, attackers can gain access to the networks of multiple organizations simultaneously. This approach not only increases the scale and impact of ransomware attacks but also complicates defense efforts, as victims may not be directly targeted and thus are less likely to be on high alert.
- Psychological Tactics and Social Engineering: RaaS affiliates often employ sophisticated social engineering tactics to trick individuals into activating ransomware. These tactics can include personalized phishing emails, scareware, or pretexting. By exploiting human psychology and organizational trust, attackers can circumvent even well-established security protocols, making RaaS campaigns more effective.
Read also: Understanding and Combating Voice Phishing aka Vishing
Futurism Technologies: Your Partner in Ransomware-as-a-Service Defense
At Futurism Technologies, we understand the gravity of RaaS threat and are dedicated to helping businesses around the globe protect their digital assets and fortify their security posture with state-of-the-art cybersecurity solutions.
- Comprehensive Security Assessments: Our team of cybersecurity experts conducts thorough security assessments to identify vulnerabilities in your systems through market-winning vulnerability and penetration testing. We employ cutting-edge tools and methodologies to assess your risk exposure to RaaS attacks.
- Advanced Threat Detection: We deploy state-of-the-art advanced threat protection solution powered by AI that can identify unusual patterns and behaviors indicative of a ransomware attack. This proactive approach helps prevent ransomware from gaining a foothold in your network.
- Email and Web Security: Most attacks take place after clicking on unknown links coming through emails or inside the websites. Futurisms’ AI enabled advanced email security and web security can help avoid cyber-attacks by warning you beforehand.
- Security Awareness Training: We believe that a well-informed workforce is a crucial line of defense. Our tailored cybersecurity awareness training programs educate your employees about the latest cyber threats, including RaaS, and how to recognize and respond to them.
- Backup and Recovery Solutions: We implement robust backup and recovery solutions to ensure that your critical data is secure and readily restorable in the event of a ransomware attack, all from our state-of-the-art Security Operations Center.
- Endpoint Protection: Endpoint is the place which can be the door for many Ransomware attacks, use of managed extended detection and response (XDR) solutions can detect and block ransomware attacks in real-time.
- Incident Response Planning: In the unfortunate event of a ransomware incident, our incident response team is well-prepared to guide you through the recovery process, negotiate with attackers if necessary, and help you make informed decisions.
- Ransomware-Specific Solutions: We offer specialized cybersecurity solutions to combat the threat of Ransomware-as-a-Service. Our experts are well-versed in the latest ransomware variants and can tailor our strategies accordingly.
You might also want to read: Hardening Your Attack Surface – A CEO/CTO Perspective in Banking Sector
Takeaway
Ransomware-as-a-Service (RaaS) is a formidable cyber threat that demands vigilant and a comprehensive defense strategy. At Futurism Technologies, we are committed to equipping our clients with the right set of security layers and tools and knowledge necessary to navigate this evolving threat landscape. We understand that digital transformation is crucial for the success of your business, but it should not come at the expense of security. Together, we can fortify your digital future and ensure that you remain resilient in the face of RaaS attacks.
Contact us today to learn more about our coming-of-age managed cyber security solutions and how we can safeguard your organization from RaaS attacks.
Subscribe Now!
TRENDING POSTS
-
The Role of AI in Construction Safety
-
What Is Predictive Maintenance and Why Does It Matter?
-
What is Ransomware-as-a-Service (RaaS)? Everything You Need To Know
-
The Role of Smart Maritime IoT Solutions in Enhancing Maritime Safety
-
Revolutionizing Telecom with AI-Driven Network Slicing
-
Data Integration Unlocked: From Silos to Strategy for Competitive Success
-
Navigating the Shadows: Understanding Zero-Click Attacks in the Digital Age
-
AI Reimagined: Crafting Next-Gen AI Apps with Expert Fine-Tuning
-
Futurism AI: Turning Ideas into Apps at Lightning-Fast Speed
-
Accelerate AI Across Your Enterprise With Futurism AI
-
Flying into the Future: How AI is Redefining the Future of Aviation
-
Beyond Intelligence: The Rise of Self-Healing AI
-
The Indispensable Role of a Trusted Offshore AI Company in 2024 & Beyond
-
IoT-Powered Smart Warehouse Management: A Detailed Guide
-
Turning Data into Dollars: The Futurism Path to AI-Driven Success
-
5 Ways to Prepare Your Business for Digital Transformation
-
4 Ways To Win at Digital Transformation on a Shoestring Budget
-
Why AI in Digital Marketing is the Next Big Thing?
-
How AI Will Enable Faster Adaptation of Digital Transformation
-
How Is Digital Modernization Important In Supplier On-Boarding?
-
Top 10 Email Marketing Tips for This Holiday Season
-
Benefits of using ERP Software for Energy and Gas Industries
-
5 Features of Supply Chain Management Software