It’s Critical Infrastructure Security and Resilience Month: How Secure is your Business?

Futurism Technologies
November 30, 2023 - 2.2K
5 Min Read
Critical Infrastructure Security and Resilience Month (CISRM) is a national awareness campaign that highlights the importance of protecting the nation’s critical infrastructure from cyberattacks. This year’s CISRM theme is “See Something, Say Something: Protecting Critical Infrastructure from Cyber Threats”.
Critical infrastructure includes things like the power grid, water systems, transportation networks, and financial markets. A cyberattack on critical infrastructure could have a devastating impact on the economy and public safety.
The Biden administration has declared November 2023 as Critical Infrastructure Security and Resilience Month. This is an opportunity to raise awareness of the importance of critical infrastructure security and to encourage organizations to take steps to protect their systems and assets.
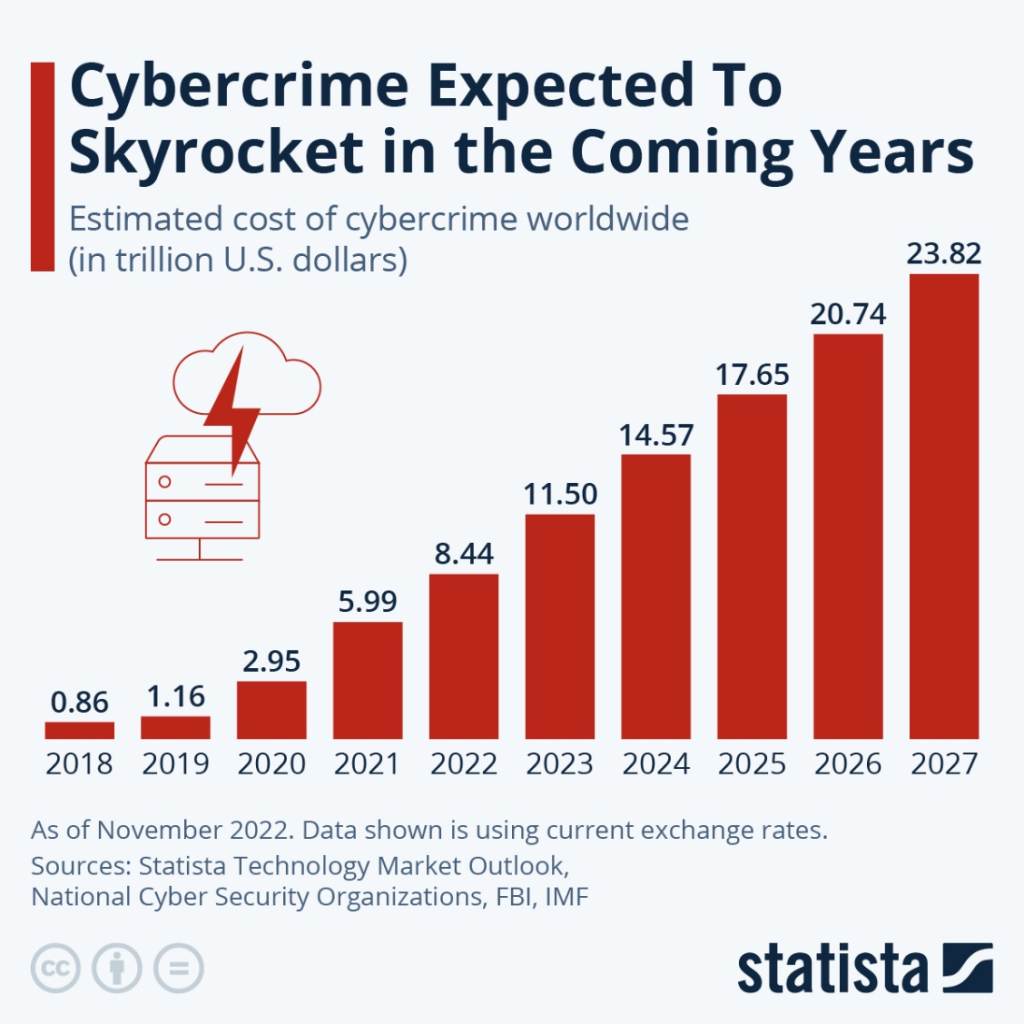
Important Points about Critical Infrastructure Security:
1. Regular Security Audits and Assessments: Conduct Vulnerability assessments to identify vulnerabilities in networks, systems, and applications on a regular basis. Frequent assessments provide insights into potential weaknesses that can be addressed promptly.
2. Patch Management and Updates: Ensure all software, applications, and systems are regularly updated with the latest patches and security updates. Timely installation of patches helps mitigate known vulnerabilities that cyber attackers may exploit.
3. Data Encryption and Secure Communication Protocols: Employ robust encryption methods for sensitive data both at rest and in transit. Implement secure communication protocols like HTTPS, VPNs, and encrypted email to safeguard critical information from unauthorized access.
4. Employee Training and Awareness: Continuous education and training programs for employees on cybersecurity best practices are pivotal. This includes recognizing phishing attempts, using strong passwords, and understanding social engineering tactics to prevent inadvertent breaches.
5. Implementing a Zero Trust Security Model: Embrace a Zero Trust approach, where no user or device is automatically trusted within the network. This model validates and verifies every access request, enhancing security by limiting lateral movement in case of a breach.
6. Incident Response Plan and Drills: Develop and regularly test an incident response plan to handle cyber incidents efficiently. Conduct drills simulating various cyberattack scenarios to ensure readiness and minimize downtime in the event of an actual breach.
7. Access Control and Least Privilege: Enforce strict access controls and follow the principle of least privilege. Grant users access only to the resources necessary for their roles, reducing the attack surface and limiting potential damage from compromised accounts.
8. Continuous Monitoring and Threat Intelligence: Implement robust monitoring systems coupled with threat intelligence feeds to detect and respond to threats in real-time. Proactive monitoring helps in early threat detection and swift response to potential breaches.
9. Backup and Recovery Strategies: Regularly back up critical data and systems. Establish effective recovery strategies to restore operations swiftly in case of a successful cyberattack or system failure.
10. Third-Party Risk Management: Assess and manage the cybersecurity posture of third-party vendors and partners. Ensure they adhere to robust security measures to prevent indirect vulnerabilities within your infrastructure.
Using a well-rounded cybersecurity strategy that combines these methods can greatly strengthen an organization’s ability to deal with evolving cyber threats, protecting vital infrastructure from potential risks.
Learn more about: The Rise of Backdoor Attacks! How Secure is your Business?
Futurism Technologies: Your Trusteed Cybersecurity Partner
We at Futurism Technologies are committed to helping organizations protect their critical infrastructure from cyber-attacks. We offer a number of managed cybersecurity solutions, including AI-powered advanced threat protection (SIEM), Zero Trust security, endpoint security, IoT security, XDR, vulnerability management, incident response and more.
We believe that critical infrastructure security is a shared responsibility. Organizations, government, public and private sector need to work together to fight the menace of cyberattacks and cybercrimes on a global scale.
Futurism technologies is committed to helping organizations protect their IT infrastructure not only during the critical infrastructure security and resilience month, but also throughout the year.
Don’t wait for the bait! Get help now. Contact us today!
Subscribe Now!
TRENDING POSTS
-
Futurism Returns to Hannover Messe 2024: Leading the Charge in Industrial and Digital Transformation
-
The Role of Smart Maritime IoT Solutions in Enhancing Maritime Safety
-
Data Integration Unlocked: From Silos to Strategy for Competitive Success
-
Navigating the Shadows: Understanding Zero-Click Attacks in the Digital Age
-
AI Reimagined: Crafting Next-Gen AI Apps with Expert Fine-Tuning
-
Explore Next-Gen Digital Solutions with Futurism at MWC 2024
-
Futurism Unleashes the Technology of Tomorrow at MWC Barcelona 2024
-
Futurism AI: Turning Ideas into Apps at Lightning-Fast Speed
-
Accelerate AI Across Your Enterprise With Futurism AI
-
Futurism to Address the Biggest Security Challenges at RSS 2022
-
Futurism at SelectUSA 2022: Steering the Next Wave of Businesses
-
Futurism to Uplift the MSP Business Community at the MSP Expo 2022
-
Futurism Sets Out to Address the Biggest Security Challenges at the RSA Conference 2022
-
5 Ways to Prepare Your Business for Digital Transformation
-
4 Ways To Win at Digital Transformation on a Shoestring Budget
-
Futurism: Empowering MSPs at the Channel Partners Conference & Expo 2022
-
Why AI in Digital Marketing is the Next Big Thing?
-
Futurism brings ‘Mobile First Digital Transformation’ to the fore at MWC Barcelona 2022
-
Cybersecurity for Rural Hospitals: How can Rural Hospitals become Cyber Smart?
-
Futurism Empowers Rural Health Care Community at the AHA Rural Health Care Leadership Conference
-
The Biggest Problem With Cybersecurity In Healthcare Sector, And How IBM QRadar Can Fix It?
-
How IBM MaaS360 is Revolutionizing Endpoint Security in the Healthcare Industry?
-
Futurism to Present its MSP Partner Program at the Channel Partners Conference & Expo 2021
-
EndPoint Security in Healthcare Matters and IBM MaaS360 Can Help
-
How AI Will Enable Faster Adaptation of Digital Transformation
-
How Is Digital Modernization Important In Supplier On-Boarding?
-
Top 10 Email Marketing Tips for This Holiday Season
-
Benefits of using ERP Software for Energy and Gas Industries