What is Vishing? Understanding and Combating Voice Phishing

Futurism Technologies
October 11, 2023 - 3.2K
5 Min Read
In today’s digital age, where cyber threats are evolving at an unprecedented rate, one particular form of cybercrime has gained significant traction: Vishing. Yes, vishing aka voice phishing, is a sophisticated cyber scam that leverages phone calls and voicemails to extract confidential and corporate information. As we delve deeper into the world of vishing, it’s crucial to understand its mechanisms, examples, and preventive measures to safeguard ourselves and our organizations.
What is Vishing?
Vishing is a cybercrime variant of phishing. Instead of using emails or malicious websites, scammers use phone calls to deceive their targets. These calls often sound legitimate, with fraudsters impersonating bank officials, tech support agents, or even government representatives. Their primary objective? To manipulate individuals into revealing sensitive information, such as bank account details, passwords, or personal identification numbers.
Did you know?
Americans lost over $68.4 million to vishing attacks and scams in 2022.
The Mechanics of a Vishing Attack
Initial Contact:
The scam begins with an unsolicited phone call. The scammer might use caller ID spoofing to appear as a legitimate entity.
Creating a Narrative:
The fraudster crafts a compelling story. It could be a fabricated tale about a compromised bank account, a tax evasion charge, or a computer security breach.
Extraction of Information:
The scammer persuades the victim to divulge confidential information. This could range from bank details to personal identification numbers.
Real-world Examples of Vishing
Bank Impersonation: A scammer might call posing as a bank representative, claiming there’s been suspicious activity on the victim’s account. They might ask the victim to confirm their account details for “verification purposes.”
Tech Support Scams: The victim receives a call from someone claiming to be from a well-known tech company, stating that their computer has a virus. The scammer then asks for remote access to the computer to “fix” the issue.
Read also: Hackers Pose as Cybersecurity Firms in New Callback Phishing Attack

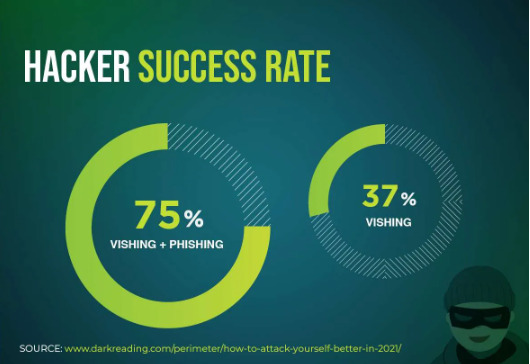
(Image source: CrowdStrike)
Preventing Vishing: Best Practices
- Be Aware of Social Engineering Tactics: Scammers often exploit human emotions like fear, greed, and trust. Being aware of these tactics can help you identify and avoid vishing attempts.
- Employee Training Conduct regular training sessions for employees to educate them about vishing tactics and how to recognize suspicious calls or emails.
- Caller Verification: Implement a policy where employees are encouraged to verify the identity of any caller requesting sensitive information, especially if the call was unsolicited.
- Use Secure Communication Channels: Encourage the use of encrypted and secure communication channels for any official communication that involves sharing sensitive data.
- Regular Updates: Keep all systems, software, and security protocols updated to the latest versions to prevent any potential vulnerabilities.
- Two-Factor Authentication: Deploy a powerful identity & access management solution or two-factor authentication for accessing sensitive data, making it harder for scammers to gain unauthorized access.
- Internal Awareness Campaigns: Regularly share updates about the latest vishing scams and tactics with employees through newsletters, emails, or internal communication platforms.
- Incident Reporting System: Establish a clear protocol for employees to report suspicious calls, and ensure that these reports are analyzed for patterns and shared with relevant teams.
- Limit Information Sharing: Minimize the amount of publicly available information about your organization and employees, as scammers often use this data to make their calls seem more legitimate.
- Simulated Vishing Drills: Conduct mock vishing attacks to test employees’ awareness and preparedness, providing feedback and training based on the results.
- Get Expert Help: Partner with a reputed managed cybersecurity services provider to deploy a powerful line of defense against vishing attacks.
- Regular Audits: Conduct regular security audits vulnerability assessment and penetration testing to identify and rectify any potential vulnerabilities in your systems.
- Clear Protocols: Establish clear protocols for financial transactions, ensuring that fund transfers or sharing of financial details never happens based solely on a phone call.
- Feedback Loop: Create a feedback loop where any vishing attempt, whether successful or not, is analyzed to improve defenses and strategies.
- External Communication: Inform customers and partners about your communication protocols, ensuring they are wary of any calls claiming to be from your organization and asking for sensitive information.
- Stay Updated: Keep abreast with latest cybersecurity news to learn about latest vishing techniques and trends in the cybersecurity world, adapting your defenses accordingly.
Takeaway
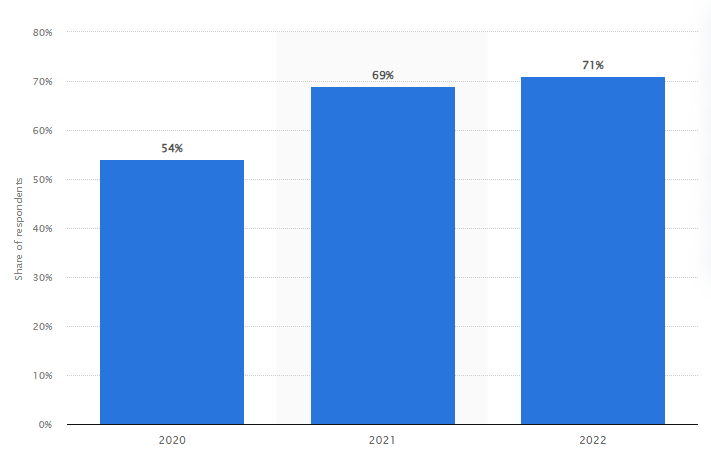
According to a report, there has been a significant rise in vishing attacks over the past few years. The report highlights that over 30% of cyberattacks in the last year had a vishing component. This emphasizes the growing threat and the need for awareness and preventive measures.
Vishing is not just another scam; it’s a sophisticated cybercrime that’s on the loose. As technology advances, so do the tactics of these scammers. Remember, when in doubt, it is always advisable to seek expert assistance.
Don’t let your organization fall victim to the rising threat of vishing attacks. Equip yourself with the right set of tools, resources and threat intel to combat this sophisticated cybercrime. At Futurism Technologies, we’re dedicated to helping you stay one step ahead of cyber threats.
Subscribe Now!
TRENDING POSTS
-
Futurism Returns to Hannover Messe 2024: Leading the Charge in Industrial and Digital Transformation
-
The Role of Smart Maritime IoT Solutions in Enhancing Maritime Safety
-
Data Integration Unlocked: From Silos to Strategy for Competitive Success
-
Navigating the Shadows: Understanding Zero-Click Attacks in the Digital Age
-
AI Reimagined: Crafting Next-Gen AI Apps with Expert Fine-Tuning
-
Explore Next-Gen Digital Solutions with Futurism at MWC 2024
-
Futurism Unleashes the Technology of Tomorrow at MWC Barcelona 2024
-
Futurism AI: Turning Ideas into Apps at Lightning-Fast Speed
-
Accelerate AI Across Your Enterprise With Futurism AI
-
Futurism to Address the Biggest Security Challenges at RSS 2022
-
Futurism at SelectUSA 2022: Steering the Next Wave of Businesses
-
Futurism to Uplift the MSP Business Community at the MSP Expo 2022
-
Futurism Sets Out to Address the Biggest Security Challenges at the RSA Conference 2022
-
5 Ways to Prepare Your Business for Digital Transformation
-
4 Ways To Win at Digital Transformation on a Shoestring Budget
-
Futurism: Empowering MSPs at the Channel Partners Conference & Expo 2022
-
Why AI in Digital Marketing is the Next Big Thing?
-
Futurism brings ‘Mobile First Digital Transformation’ to the fore at MWC Barcelona 2022
-
Cybersecurity for Rural Hospitals: How can Rural Hospitals become Cyber Smart?
-
Futurism Empowers Rural Health Care Community at the AHA Rural Health Care Leadership Conference
-
The Biggest Problem With Cybersecurity In Healthcare Sector, And How IBM QRadar Can Fix It?
-
How IBM MaaS360 is Revolutionizing Endpoint Security in the Healthcare Industry?
-
Futurism to Present its MSP Partner Program at the Channel Partners Conference & Expo 2021
-
EndPoint Security in Healthcare Matters and IBM MaaS360 Can Help
-
How AI Will Enable Faster Adaptation of Digital Transformation
-
How Is Digital Modernization Important In Supplier On-Boarding?
-
Top 10 Email Marketing Tips for This Holiday Season
-
Benefits of using ERP Software for Energy and Gas Industries