The Ultimate Cybersecurity Checklist for Hospitals in 2021 and Beyond – A Futurism Advisory

Futurism Technologies
September 9, 2021 - 1.2K
5 Min Read
Amidst the pandemic and fragile global economy, the last thing a hospital would want is the expense and nightmare of dealing with a vicious cyberattack.
According to IBM, data breaches caused the healthcare industry to lose a staggering $7.13 million in 2020. Cyber attacks on healthcare organizations are expected to grow 5x by 2021, say experts. Healthcare is one of the prime targets for hackers, threat actors and malicious cyber groups looking to disrupt care operations and achieve unethical gains.
In addition, an increasing number of cybercriminals are targeting global COVID-19 response organizations including pharmaceutical companies, hospitals, medical supplies companies, etc. disrupting relief and supply chain efforts worldwide.
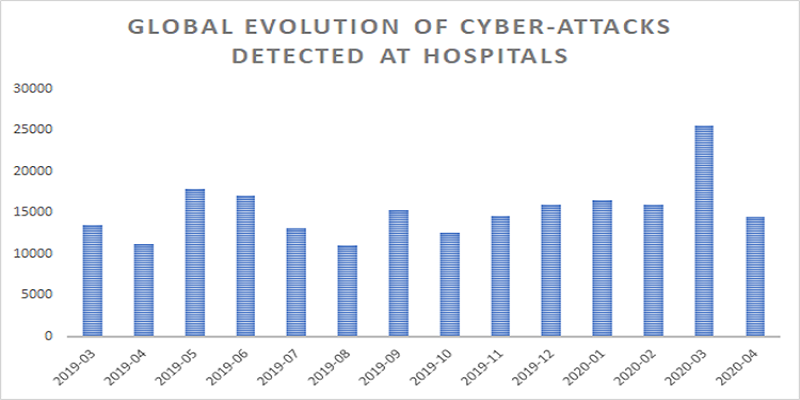
(Source: Security Boulevard)
Cybercriminals target healthcare, because it is a highly lucrative industry and deals with sensitive patient and medical data. This data can be used for several unethical purposes such as blackmailing the patients, phishing attacks, buying prescription medications, generating fake insurance claims, etc.
The real threat lies in plain sight
Healthcare organizations and providers have certain attributes that make them easy targets for cybercriminals and malicious threat actors. For instance, unpatched and/or outdated networks, devices, OS and systems serve as the perfect gateways for hackers to execute successful breaches or attacks. This is just the tip of iceberg as we see it, as there lies a streak of vicious cyber threats beneath. The reason cybersecurity has become mission-critical for healthcare organizations and providers across the world.
Hospitals, clinics and other healthcare organizations face a number of IT security risks and issues throughout the year. Here we explore five alarming signs or scenarios in your hospital or healthcare organization that scream of an impending cyberattack.
5 Signs that Indicate an Impending Data Breach
1. Frequent influx of phishing or suspicious emails

Did you know? According to HIPAA, 60% of healthcare data breaches involve phishing or some kind of email attack.
Phishing undeniably is the most common attack techniques used to compromise healthcare organizations across the world. Attackers often tend to pose as a pharmacy, healthcare provider or an insurance firm to send out phishing emails to patients. The message in the email may ask patients to furnish personal details or ask them to download some attached file, document, etc.
Similarly, these bad guys send out phishing emails to healthcare workers or staff posing as their colleagues or patients asking them to click on certain links or download unsafe attachments.
Such links or attachments often contain malware infecting the hospital’s IT environment thus, helping hackers gain unethical access to databases, systems, devices and networks.
2. Unpatched systems

Almost half of data breaches at healthcare organizations could’ve been prevented with timely patching. (Source: ZDNet)
Unpatched vulnerabilities expose sensitive patient information and critical business information and systems to malicious threat actors. The key to protect networks exposed to cybercriminals is to apply patches as and when they are released, especially the ones designed and rolled-out to fix critical vulnerabilities.
Many hospitals run on legacy security systems that are often fail to receive automatic patch updates leaving them vulnerable to attacks and breaches. Now replacing these legacy systems is often an expensive and time-consuming task for many hospitals due to lack of budget and skills in-house. This is where a managed security services provider comes into action. Futurism EndPoint Secure developed with IBM Maas360 is a managed endpoint security service offering that offers the right layers of security and resources for your hospital to help manage all your endpoints in a cost-effective way.
Unpatched systems have led to some of the most lethal attacks in the history of cybersecurity and healthcare is no exception. Further, lack of ownership or misconfiguration may lead to weak encryption on networks, devices, and databases of a hospital thus, stressing the need of engaging a specialized and trusted managed security services provider to deal with these incidents.
Developed in collaboration with IBM, Futurism EndPoint Secure helps a hospital to deploy powerful asset monitoring and discovery practice in place to achieve better visibility into the rapidly expanding attack surfaces of a hospital that include connected medical devices, IoT devices/systems, cloud apps, remote connections, BYOD, etc.
Read also: EndPoint Security in Healthcare Matters and how Futurism and IBM MaaS360 can help
3. Weakly protected servers, EHRs and digital front doors (websites, apps, etc.)

Databases and web servers of healthcare organizations contain tons of sensitive data. This includes electronic health records or EHRs, employee data, intellectual property, and drug and research information. Hackers are always on the lookout for misconfigured, vulnerable or weakly protected servers and databases to steal such data.
Healthcare database and websites often become victims of SQL injections, DDoS attacks and brute force attacks if they:
- Lack certified cybersecurity skills and resources
- Lack access to threat intelligence
- Run unpatched or obsolete hardware and software
- Do not monitor risky remote connections
- Fail to monitor app vulnerabilities
New and advance threat actors emerge on daily basis posing serious threats to healthcare organizations. Thus, healthcare businesses ought to have a detailed digital transformation roadmap when it comes to security. There are several aspects in a care delivery process and thus, digital transformation in healthcare is incomplete without cybersecurity.
4. Unsecured mobile devices and medical equipment

The moment a healthcare personnel goes mobile, the threat surface widens automatically and drastically, which is one of the biggest concerns for any healthcare organization today. In addition, when we talk about BYOD policies in healthcare, it is important to take into consideration the various security parameters when enabling healthcare personnel access to different medical systems and records. Malicious or suspicious network traffic unauthorized access and configuration vulnerabilities are often the most common entry points for cybercriminals.
Healthcare organizations are a virtual jackpot of medical and health data. Hospitals today greatly rely on connected medical equipment and devices to diagnose as well as treat patients. Unfortunately, many of these connected medical devices lack robust security controls, run on unpatched or outdated software, etc. making them vulnerable to breaches.
Further, the influx of IoT (Internet of Things) and IoMT i.e. Internet of Medical Things into the healthcare sector gives cyber criminals a gigantic pool of insecure and connected medical devices to target and penetrate into a hospital’s IT and network environment.
Did you know? According to Ordr, a whopping 5 million unmanaged IoMT and IoT medical devices were found to be running on obsolete technology and lacked advance threat defenses.
Hackers after successfully breaking into such insecure connected devices can move laterally throughout a hospital’s network to take full control of all critical endpoints and cripple the hospital’s entire IT environment disrupting care delivery and causing delays in treatments endangering lives. They may also encrypt or steal patient sensitive information for Ransomware attacks.
5. Lack of documented cybersecurity policies and basic IT/security hygiene

Cyber hygiene is necessary for all organizations and healthcare is no exception. HIPAA Security Rule mandates healthcare providers to adopt appropriate and reasonable policies and protocols to prevent security incidents.
A healthcare organization ought to periodically update and review their cybersecurity documentation on how it handles, stores and transfer electronic protected health information (EPHI). Unfortunately, not all healthcare organizations adhere to these requirements of cybersecurity procedures and policies thus, ending up in troubled waters in the event of an attack. This is one of the prime reasons for the creation of several security loopholes only to be exploited by the hackers.
Did you know? Surprisingly, most healthcare workers are given access to sensitive files on the very first day of work!
Weak or loosely monitored access control policies have often led to vicious attacks on healthcare providers. One such instance is the data breach at Mednax, Inc. wherein cybercriminals used unauthorized attack tactics to gain access to its database compromising data of some 1.3 million patients.
This is why sensitive patient information and critical health data must only be accessible to authorized personnel. Healthcare organizations ought to have stringent access control policies in place to avoid both internal as well as external threats.
Takeaway
Cyber threats do make their way onto a hospital’s network from time to time and it is essential to have the right tools, technology and people in place to keep these attacks at bay. Having a managed security services vendor by your side will double up your efforts in keeping evolving attacks at bay.
Unfortunately, healthcare industry is the most affected when it comes to cyber attacks. It is unthinkable for a hospital to afford a device shutdown or system breakdown due to an attack. These attacks and threats can shut down a hospital. With the right cybersecurity awareness and investment, a healthcare organization puts itself in a much better position to deal with these attacks in a proactive and effective manner.
We know that most healthcare providers lack the necessary skills, resources and tools to prevent these attacks. It’s time they ask for help and engage a trusted managed security services provider. With Futurism EndPoint Secure, a healthcare organization no longer requires to purchase expensive security products and resources and also don’t need to hire additional security skills. Futurism does it all for you!
To know more about how IBM and Futurism can help secure your hospital with the right layers of security, call +1 (732) 790-2593 or schedule a FREE consultation here.
Subscribe Now!
TRENDING POSTS
-
The Role of Smart Maritime IoT Solutions in Enhancing Maritime Safety
-
Data Integration Unlocked: From Silos to Strategy for Competitive Success
-
Navigating the Shadows: Understanding Zero-Click Attacks in the Digital Age
-
AI Reimagined: Crafting Next-Gen AI Apps with Expert Fine-Tuning
-
Explore Next-Gen Digital Solutions with Futurism at MWC 2024
-
Futurism Unleashes the Technology of Tomorrow at MWC Barcelona 2024
-
Futurism AI: Turning Ideas into Apps at Lightning-Fast Speed
-
Accelerate AI Across Your Enterprise With Futurism AI
-
Futurism to Address the Biggest Security Challenges at RSS 2022
-
Futurism at SelectUSA 2022: Steering the Next Wave of Businesses
-
Futurism to Uplift the MSP Business Community at the MSP Expo 2022
-
Futurism Sets Out to Address the Biggest Security Challenges at the RSA Conference 2022
-
5 Ways to Prepare Your Business for Digital Transformation
-
4 Ways To Win at Digital Transformation on a Shoestring Budget
-
Futurism: Empowering MSPs at the Channel Partners Conference & Expo 2022
-
Why AI in Digital Marketing is the Next Big Thing?
-
Futurism brings ‘Mobile First Digital Transformation’ to the fore at MWC Barcelona 2022
-
Cybersecurity for Rural Hospitals: How can Rural Hospitals become Cyber Smart?
-
Futurism Empowers Rural Health Care Community at the AHA Rural Health Care Leadership Conference
-
The Biggest Problem With Cybersecurity In Healthcare Sector, And How IBM QRadar Can Fix It?
-
How IBM MaaS360 is Revolutionizing Endpoint Security in the Healthcare Industry?
-
Futurism to Present its MSP Partner Program at the Channel Partners Conference & Expo 2021
-
EndPoint Security in Healthcare Matters and IBM MaaS360 Can Help
-
How AI Will Enable Faster Adaptation of Digital Transformation
-
How Is Digital Modernization Important In Supplier On-Boarding?
-
Top 10 Email Marketing Tips for This Holiday Season
-
Benefits of using ERP Software for Energy and Gas Industries