Eye Care Leaders EMR Breach Affects Over 1.5 M: Why Healthcare Providers Should Worry About Unsecured Partner Networks
Eye Care Leaders, a leading provider of ophthalmology-specific EHR and practice management solutions in the U.S. suffered a data breach affecting over eight different care providers and millions of individuals.
Eye Care Leaders (ECL) is caught in a perfect cyber storm. Yes! According to reports, the healthcare provider experienced a data breach, wherein the attackers accessed one of its cloud-based EMR systems deleting system configuration files and databases thus, exposing and putting sensitive data of more than 1.5 million patients at risk.
One of the affected medical group practices (Tennessee-based) said that the Eye Care Leaders breach has impacted more than 50,000 of its patients and is in the process of auditing its vendor relationship with the provider. Another Seattle-based health system that was also implicated said that the breach has affected more than 20,000 individuals and is evaluating its security posture and partner network with ECL.
The investigation is ongoing and Eye Care Leaders said that it was working closely with all its vendors to investigate and assess the incident. A single security breach can trigger immense reputational damage coupled with monetary losses and threats to PHI (Protected Health Information), said an official for ECL.
Implications:
Under The Health Insurance Portability and Accountability Act (HIPAA), all the covered entities that partner with vendors and interact with patient information must enter into a valid business associate agreement (BAA). Further, the business associate agreement lays out specific requisites for the vendor to adhere to in compliance with HIPAA to meet the relationship needs. In the case of Eye Care Leaders breach, the attack caused multiple periods of system downtime that lasted from 4-7 days.
Implications were as follows:
Multiple system outages leading to disruption in services and access to critical systems
Lost patient data and exposed PHI
Inability to serve patients/clients
HIPAA violations
Why healthcare providers should worry about unsecured partner/vendor networks?
The Eye Care Leaders breach raises serious concerns about why should healthcare providers be careful about unsecured partner/vendor networks and relationships.
To begin with, ECL is not the first healthcare provider to suffer from such attacks. However, the volumes of incidents associated with the Eye Care Leaders breach and the scope of the attack, which has impacted multiple care practices across the country affecting millions of people certainly ring a bell. There is more to this than meets the eye. This is just the tip of the iceberg as we see it, said an investigating cybersecurity engineer.
Did you know?
According to HIPAA Journal, more than 700 data breaches were recorded each day in 2021 and the figures are projected to double in the next coming years.
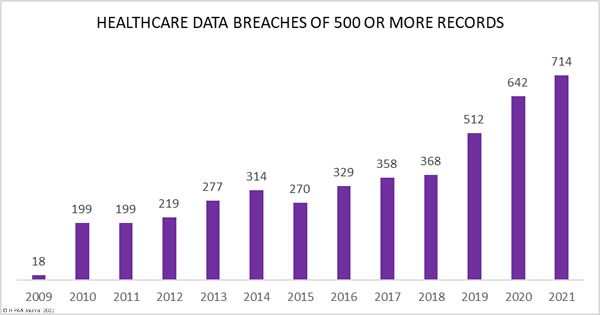
The HIPAA report serves as a stark reminder for healthcare businesses and entities to prioritize securing their partner/vendor networks and keep unauthorized access at bay. The reason is that most of these breaches were a direct result of unauthorized access to partner networks or systems exposing large volumes of sensitive patient information.
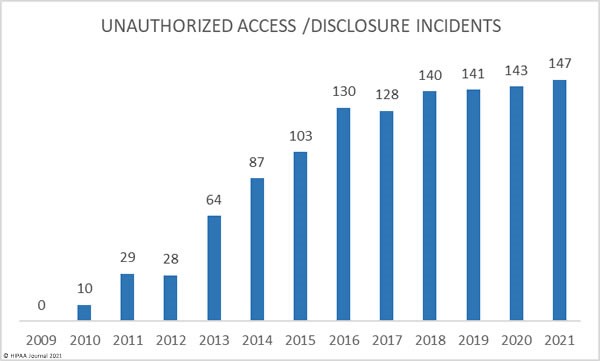
Healthcare providers often work with multiple vendors and/or partners including insurance companies, pharmaceutical companies, care practices, etc. Unfortunately, most providers often neglect and/or lack the necessary skills and resources when it comes to assessing vendor/partner networks for any underlying security vulnerabilities and risks.
HIPAA Compliance & PHI Protection Requirements for Healthcare Vendors
Being HIPAA-compliant does not validate that a healthcare provider is adequately protected against attacks and breaches. This is why healthcare providers ought to have a proactive security approach to prevent and remediate compliance-related threats.
When working with a healthcare business or care associate, to manage PHI, all the covered entities ought to enter into BAA (Business Associate Agreement), which includes specific provisions such as required security protocols for business associates and cyber incident reporting.
Now under HIPAA, healthcare providers are required to have a robust compliance program based on several federal guidelines. This includes communication, reporting and notifying cybersecurity incidents. HIPAA requires healthcare providers to assess system/network log activities on a daily basis and this is where managed security services providers come into the picture to help healthcare businesses achieve the following:
Perform comprehensive HIPAA security analysis (security log monitoring and real-time log management)
Monitor log-in attempts and report discrepancies in health information systems
Implement security audit controls and assess activities in health information systems (ePHI)
Track records of information logged into the PHI systems in real-time
Track event logs, access reports, audit logs, and incident reports
Consolidate system activity logs on a centralized server
Deploy strong security controls over logs with role-based access policies and control
File integrity monitoring
Devise HIPAA security strategy and data backup/recovery plan
Develop prompt incident response mechanism
Detect abnormal connection and network behavior (malware, worm propagation, spear phishing, etc.)
Takeaway
Eye Care Leaders breach is a stark reminder to all healthcare providers to prioritize vendor management as a part of their security risk analysis exercise or strategy. A healthcare provider cannot treat patients without vendors and the Eye Care Leaders breach proved that. However, these types of attacks serve as a strong reminder for providers to revise or reassess their relationship with their care practices and associates to ascertain that both entities are up-to-date when it comes to security.
Last but not the least, healthcare providers ought to focus on educating and training their staff with emphasis on compliance, cyber hygiene and ethics. Getting help from a trusted managed security service provider is an excellent step to preventing such incidents and staying compliant in today’s fast-evolving threat landscape.
Futurism has been helping healthcare organizations including both smaller and larger providers across the country to fortify their security architecture by providing them with the right layers of security resources and skills.
Our Managed Security Acceleration Services are designed to help healthcare providers leverage the power of market-leading Threat Intelligence (IBM) using a Zero Trust Security Model to offer up-to-the-minute protection against new-age threats and risks.
Disclaimer: All the information, views and opinions expressed in this op-ed are those of the authors and their respective web sources and in no way reflect the views, principles, or objectives of Futurism Technologies.
Futurism Technologies is a trusted Digital Transformation (DX) advisor and consulting partner helping businesses around the world to unlock the true value of digital for the last two decades. One of the fastest-growing global digital transformation companies with offices across continents including North America, Europe, the Gulf, Asia, and Australia, Futurism delivers 360-degree Digital Transformation solutions to enterprises of all sizes and verticals. We have been helping enterprises leverage advanced technologies with our tested DX solutions. Futurism takes great pride in helping businesses realize the true potential of digital by helping them leverage the most from coming-of-age technologies such as Artificial Intelligence (AI), Machine Learning (ML), Robotic Process Automation (RPA), 5G, IoT, Data Science/Big Data, Cybersecurity, Blockchain, Mobility, Product Engineering, Cloud, and more.
Make your business more successful with latest tips and updates for technologies