Keep the ‘Middle Man’ Out: How to Safeguard Your SaaS Infrastructure!

Futurism Technologies
October 22, 2025 - 1.2K
5 Min Read
Did you know that 76% of organizations globally have experienced a Man-in-the-Middle (MITM) attack, and 69% of those attacks are successful? As businesses increasingly move to the cloud and adopt Software as a Service (SaaS) solutions, the risk of such cyber threats continues to rise. But don’t panic there’s plenty you can do to safeguard your company’s data and reputation.
At Futurism Technologies, we understand the importance of securing your SaaS infrastructure, especially when sensitive information is at stake. Whether you’re in BFSI, healthcare, eCommerce, or any other vertical, protecting your customers’ data and maintaining business continuity is essential.
In this blog, we’ll explore what MITM attacks are, how they can affect your enterprise, and, most importantly, how to prevent them. Let’s dive in!
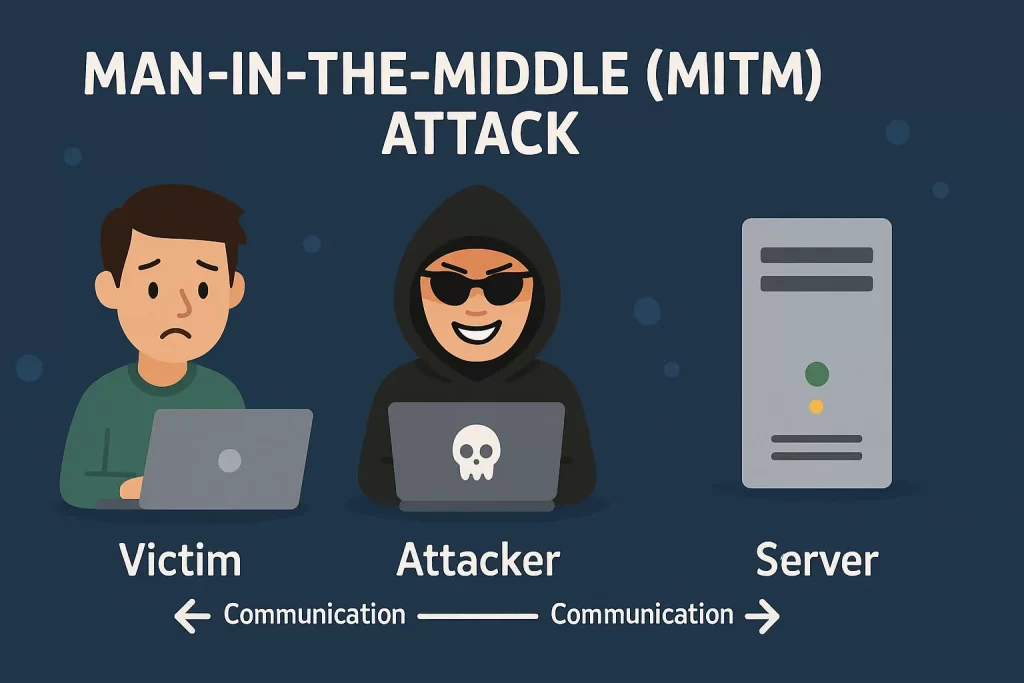
What is a Man-in-the-Middle (MITM) Attack?
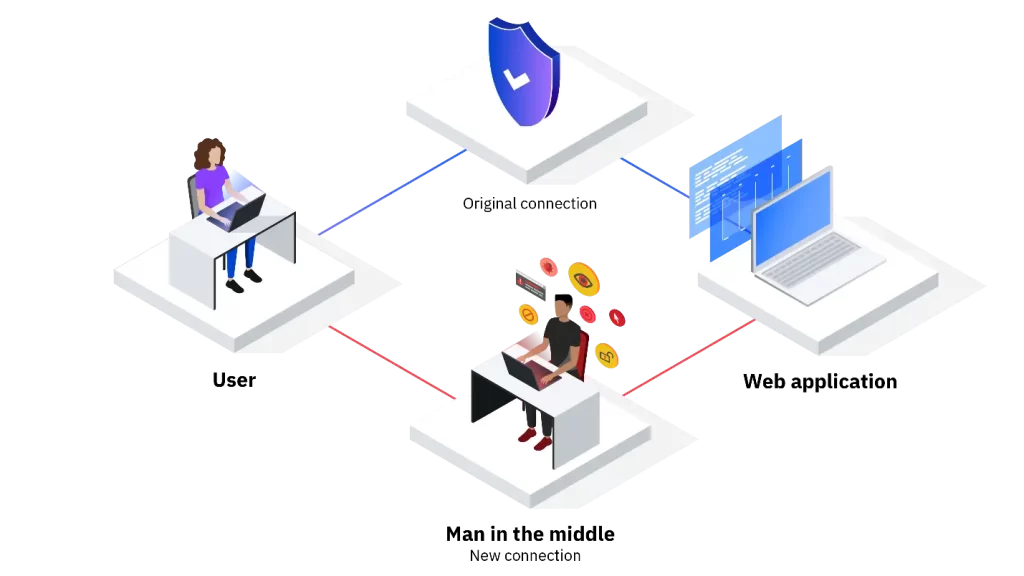
In simple terms, a Man-in-the-Middle (MITM) attack occurs when a malicious actor secretly intercepts and manipulates communication between two unsuspecting parties. These parties are typically your employees or customers and your SaaS platform. The attacker sits in the middle of the conversation, often without either party realizing it, and can steal sensitive information like login credentials, credit card numbers, and confidential corporate data.
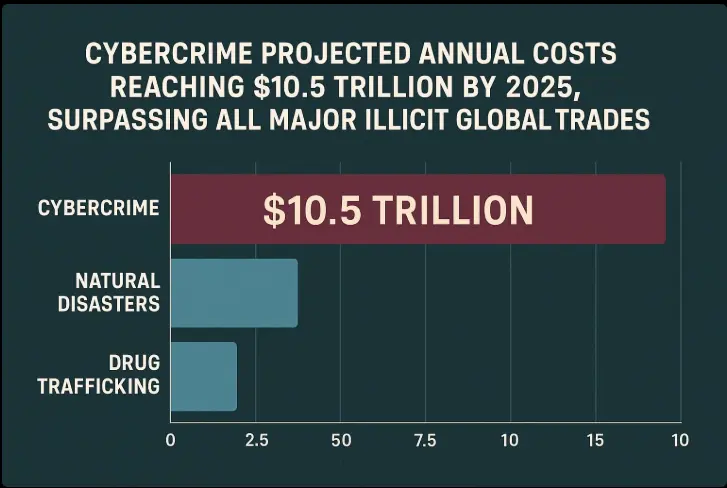
Why does this matter? A recent market analysis predicts that cybercrime will result in global economic losses of $10.5 trillion annually by 2025, with MITM attacks being one of the leading factors contributing to this rise.
In the fast-paced digital world, where businesses increasingly rely on cloud services, ensuring the security of your communication channels isn’t just important it’s non-negotiable.
To stay ahead of evolving threats, it’s crucial to strengthen your security framework, and our detailed guide on IoT security can help you get started on the right path. Explore the guide here.
The Growing Threat to SaaS Solutions
As organizations transition to cloud-based services and SaaS platforms, they open new doors for innovation and growth. However, this transition also brings a heightened vulnerability to cyberattacks. MITM attacks exploit vulnerabilities in network communication, especially over unsecured Wi-Fi networks or weak encryption protocols.
For enterprise-level organizations, the consequences of a successful MITM attack can be catastrophic:
- Data Breaches: Stolen login credentials, proprietary business information, and financial data.
- Financial Losses: Fraudulent transactions and theft of funds.
- Loss of Customer Trust: Customers expect their data to be secure. A security breach can lead to irreparable brand damage.
In fact, according to Cybersecurity Report, 95% of companies in the U.S. report that they’ve been targeted by cyberattacks, with MITM attacks being among the most common.
To fortify your defenses against these evolving threats, explore our comprehensive blog on how AI is transforming cybersecurity and empowering businesses to stay one step ahead. Read the full blog here.
Key MITM Attack Vectors in the SaaS Industry
- Unsecured Wi-Fi Networks
- Public Wi-Fi networks are notoriously insecure. Attackers can easily set up rogue access points in places like coffee shops, airports, and co-working spaces. Once a user connects, the attacker can intercept data, including passwords and sensitive business information, between the user and the SaaS platform.
- DNS Spoofing and ARP Spoofing
- Domain Name System (DNS) spoofing occurs when an attacker manipulates DNS records to redirect traffic through malicious servers. Similarly, ARP (Address Resolution Protocol) spoofing can redirect communications between users and SaaS servers. Both can easily result in MITM attacks.
- SSL/TLS Stripping
- SSL/TLS encryption is designed to secure communication between browsers and servers. However, attackers can perform SSL/TLS stripping, which downgrades the secure connection to an unencrypted one, allowing them to intercept data before its encrypted.
- Session Hijacking
- In this type of attack, attackers steal a valid session token to impersonate a user and gain unauthorized access to applications or data.
The Impact of MITM Attacks on Your Business
Understanding the potential impact of MITM attacks on your business is key to prioritizing security in your SaaS infrastructure. Here are a few reasons why safeguarding your enterprise against MITM attacks is crucial:
1. Reputation Damage
In an age where data privacy and security are top priorities for consumers, a MITM attack can severely damage your reputation. Customers trust you with their data, and a breach can result in lost clients and negative media attention. 87% of consumers say they would stop doing business with a company after one data breach.
2. Regulatory Fines
Various sectors, such as healthcare and finance, are governed by stringent data protection regulations. A MITM attack that results in a breach could mean hefty fines and legal consequences for non-compliance.
3. Financial Losses
The direct costs of a MITM attack can be staggering. Insurance premiums increase, customer compensations are required, and IT resources are drained during recovery.
4. Operational Disruption
After a successful MITM attack, your SaaS platform may experience significant downtime, service interruptions, or even loss of data, all of which can affect business continuity and productivity.

How to Prevent MITM Attacks in Your SaaS Infrastructure
At Futurism Technologies, we specialize in end-to-end digital transformation and secure AI/IoT integration. We recognize that preventing MITM attacks demands a comprehensive, multi-faceted strategy. Here are some strategies you can implement to protect your enterprise:
1. Enforce HTTPS and TLS Encryption
HTTPS should be the default for all communication. TLS encryption guarantees that data stays secure and unchanged while being transmitted. Always use Strong HTTPS protocols and TLS certificates to prevent attackers from intercepting communication.
2. Use Multi-Factor Authentication (MFA)
Implementing MFA adds an extra layer of security. Even if an attacker intercepts login credentials, they won’t be able to access your system without the additional verification code. According to Microsoft, MFA can block 99.9% of automated attacks.
3. Deploy DNSSEC (DNS Security Extensions)
DNSSEC is a security mechanism created to safeguard against DNS spoofing attacks. By implementing DNSSEC, you ensure the authenticity of your DNS queries, reducing the likelihood of redirection to malicious websites.
4. Leverage Certificate Pinning
Certificate pinning helps ensure that your users’ applications only trust specific certificates. This prevents attackers from using forged certificates to impersonate legitimate services. It’s an essential tool for defending against MITM attacks in mobile apps.
5. Regular Security Audits and Penetration Testing
Conducting frequent security audits and penetration tests is crucial for identifying potential vulnerabilities in your SaaS infrastructure. Vulnerability assessments can help identify weak points in your system before an attacker can exploit them.
6. Educate Your Teams and Customers
A strong defense against MITM attacks requires constant vigilance. Educate your employees and customers on the risks of using unsecured networks, how to spot phishing attacks, and the importance of secure passwords.
Conclusion:
MITM attacks are a growing threat, but with the right security strategies, you can protect your enterprise and its data. At Futurism Technologies, we help organizations implement secure, scalable solutions that drive growth while safeguarding against cyber risks.
By adopting a multi-layered security approach, you can keep your SaaS platform secure and trusted by your customers. Ready to secure your infrastructure and navigate digital transformation with confidence? Contact Futurism Technologies today to learn how we can protect your enterprise against evolving cyber threats.
Subscribe Now!
TRENDING POSTS
-
Agentic AI and Generative AI: What’s Best for Your Business?
-
Deepfake Scams: How to Protect Your Business in the Age of AI
-
AI and Cybersecurity: A Strategic Guide for C-Suite Leaders in 2025
-
How Location Intelligence is Revolutionizing BFSI: 6 Must-Know Benefits
-
Cloud and Data Engineering: The Path to Faster Insights and Smarter Decisions
-
From Delays to Innovation: How AI is Optimizing the Construction Industry
-
Data-Driven Future: 6 Trends to Watch Out For
-
The Impact of IoT on Reducing Maritime Carbon Footprints
-
Demystifying SASE: What is Secure Access Service Edge?
-
The Role of AI in Construction Safety
-
What Is Predictive Maintenance and Why Does It Matter?
-
What is Ransomware-as-a-Service (RaaS)? Everything You Need To Know
-
The Role of Smart Maritime IoT Solutions in Enhancing Maritime Safety
-
Revolutionizing Telecom with AI-Driven Network Slicing
-
Data Integration Unlocked: From Silos to Strategy for Competitive Success
-
Navigating the Shadows: Understanding Zero-Click Attacks in the Digital Age
-
AI Reimagined: Crafting Next-Gen AI Apps with Expert Fine-Tuning
-
Futurism AI: Turning Ideas into Apps at Lightning-Fast Speed
-
Accelerate AI Across Your Enterprise With Futurism AI
-
Flying into the Future: How AI is Redefining the Future of Aviation
-
Beyond Intelligence: The Rise of Self-Healing AI
-
The Indispensable Role of a Trusted Offshore AI Company in 2024 & Beyond
-
IoT-Powered Smart Warehouse Management: A Detailed Guide
-
Turning Data into Dollars: The Futurism Path to AI-Driven Success
-
5 Ways to Prepare Your Business for Digital Transformation
-
4 Ways To Win at Digital Transformation on a Shoestring Budget
-
Why AI in Digital Marketing is the Next Big Thing?
-
How AI Will Enable Faster Adaptation of Digital Transformation
-
How Is Digital Modernization Important In Supplier On-Boarding?
-
Top 10 Email Marketing Tips for This Holiday Season
-
Benefits of using ERP Software for Energy and Gas Industries
-
5 Features of Supply Chain Management Software





