Twitter’s ‘Blue Tick’ Chaos Triggers New Spear Phishing Campaign
Halloween may have passed, but things are turning a lot scary for Twitter users worldwide, since they’re prone to a new-age spear-phishing attack campaign.
Cybercriminals are capitalizing on Twitter’s ongoing ‘Blue Tick’ aka Verification Badge chaos by sending out phishing emails to hack the usernames and passwords of ignorant users. According to TechCrunch, the latest phishing email tactic attempts to bait Twitter users into keying in their credentials on a rigged website disguised as a Twitter help page.
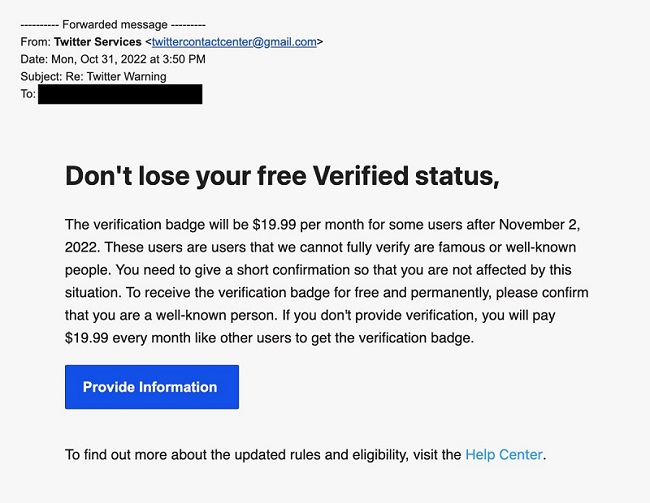
The emails were supposedly sent from a Gmail account containing links to some Google Doc that had another URL to a Google Site, which allows users to host web content. This made it difficult for Google to identify and detect the abuse through its automatic scanning mechanism/tools. However, the page had an embedded frame from another suspicious site, hosted on a Russian web hosting server, which asked for users’ passwords, usernames, and contact details. Now, this is more than enough to compromise Twitter accounts that lacked a robust multi-factor authentication (MFA).
Google has taken down the suspected phishing pages, links, and accounts citing violations of its service terms, stated a Google spokesperson. On the other hand, Twitter’s all-new CEO, Elon Musk has asked his team to speed up the revamping process of the site’s verification mechanism.
Accounts that lacked multi-factor authentication (MFA) are believed to be the most affected. Clearly, hackers are taking undue advantage of Twitter users who don’t want to pay the increased monthly subscription fee to retain their blue tick or verified badge.
Read also: Hackers Pose as Cybersecurity Firms in New Callback Phishing Attack
This spear-phishing campaign is a stark reminder that it doesn’t have to be a pandemic, hurricane, or any other calamity to trigger such a kind of cyberattack.
We recommend to lookout for the following signs to spot a phishing scam right in its tracks:
Poor grammar, often with typos (this is a hallmark of almost all phishing scams)
Often, the email is sent from an unofficial email address (e.g. Twitter##### @gmail.com), not from the official Twitter domain
Never click on suspicious links, attachments, or URLs in emails
Keep OS up-to-date and use updated firewall, anti-spam, and anti-virus solutions
Get endpoint security for all connected systems/devices and digital assets or front doors including emails, websites, desktops, mobiles, etc.
Avoid furnishing personal information to unsolicited requests
Stay updated with the latest phishing campaigns and tactics (cyber awareness)
Never share your credentials over phone
Takeaway
Though Twitter is yet to make a formal and public announcement about the future of its ‘Blue Tick’ program, it clearly hasn’t halted cybercriminals from feasting on the credentials of its users. Hackers seem to have been taking advantage of the lack of clear information from the social media giant since it went private following Elon Musk’s $44 billion takeover. Every internet disruption results in cybercriminals and hackers looking for means to take advantage and Twitter’s ‘Blue Tick’ chaos was the perfect storm.
Disclaimer: All the information expressed in this article are those of the authors and their respective sources and in no way reflect the principles, views, or objectives of Futurism Technologies.
Futurism Technologies is a trusted Digital Transformation (DX) advisor and consulting partner helping businesses around the world to unlock the true value of digital for the last two decades. One of the fastest-growing global digital transformation companies with offices across continents including North America, Europe, the Gulf, Asia, and Australia, Futurism delivers 360-degree Digital Transformation solutions to enterprises of all sizes and verticals. We have been helping enterprises leverage advanced technologies with our tested DX solutions. Futurism takes great pride in helping businesses realize the true potential of digital by helping them leverage the most from coming-of-age technologies such as Artificial Intelligence (AI), Machine Learning (ML), Robotic Process Automation (RPA), 5G, IoT, Data Science/Big Data, Cybersecurity, Blockchain, Mobility, Product Engineering, Cloud, and more.
Make your business more successful with latest tips and updates for technologies