Hundreds of SpiceJet passengers were stranded across various airports around the world due to a Ransomware attack that affected the airline’s systems and operations.
The SpiceJet attack resulted in delayed flights, tangled logistics, infuriated passengers stranded across different airports around the world and most importantly, the threat to data. The incident is yet another alarm for organizations to wake up to the call of cybersecurity in today’s fast-evolving threat landscape.
SpiceJet took cognizant of the incident stating that the breach had slowed down the departure of certain flights, as their systems faced an attempted Ransomware attack and that their IT team is working hard to contain the breach.
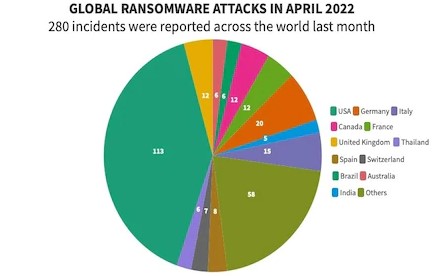
The incident has shifted the focus on the growing problem of Ransomware, which is one of the top attack types among all affecting millions of businesses around the world. All the available data suggests that Ransomware is here to stay and the best thing to do is to prepare yourself.
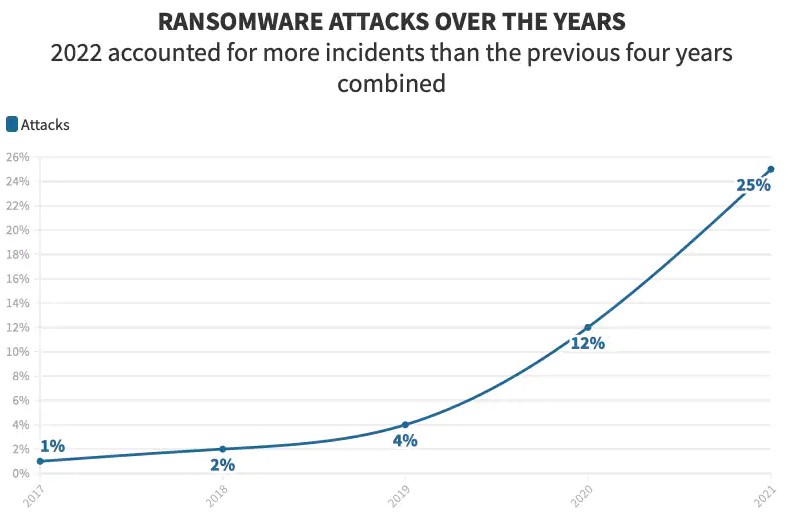
A recent report by Verizon revealed a startling 13% increase in Ransomware attacks worldwide. According to this report, Ransomware attacks saw a staggering spike in the last few years compared to other attack tactics in the last four years.
How do Ransomware attacks work?
As the name says, a Ransomware attack is an intentional attempt by cybercriminals to hold a system or computer hostage. After hacking the system successfully, the attacker will deny its target (organization) access to the system until they pay off a ransom. Attackers execute this attack by either gaining unauthorized access to a system (from remote) or tricking the target (employees) into downloading a legitimate-looking file or convincing them to click on a URL/attachment in an email, which then encrypts the files of the user and locks them out of the system.
Worst, certain advanced Ransomware attacks like the ‘WannaCry’ can transmit between systems and computers without user intervention.
According to cybersecurity experts, a hacker can unleash a Ransomware attack in the following ways:
Duplicating credentials (a widely used tactic in Ransomware attacks)
Phishing (spear-phishing)
Exploiting vulnerabilities (unpatched systems)
Lost or stolen devices
Unrestricted access policies and privileges
Weak email and web protection
Unsecured connected and mobile devices
Poor firewall and network protection
End-of-life OS/devices
Did you know?
North America accounted for the most number of system intrusion attacks (a subset of Ransomware) in 2021.
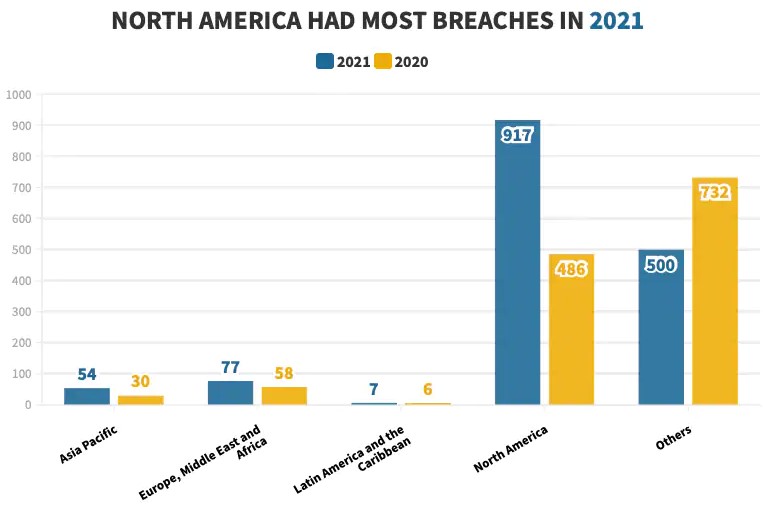
According to the report, external threat actors accounted for more than 90% of these attacks, whereas credentials were stolen in more than 40% of these incidents and personal data was compromised in more than 35% of the cases.
How to stop Ransomware in its tracks?
A recent Wall Street Journal report unfolded some gruesome facts pertaining to the cost and repercussions of Ransomware attacks on businesses worldwide. Ransomware attacks resulted in a total shutdown for many unfortunate businesses for weeks. In fact, some organizations had to retort to paper documentation until they were able to rebuild or restore their systems.
Businesses ought to track Ransomware in its tracks before it turns lethal.
Unlike other attack types, a Ransomware attack is quite straightforward. The foremost defense strategy for a business to thwart these attacks is to encrypt the data and make it inaccessible to an unauthorized entity by having powerful access-based privileges and policies.
Strong firewall and vigilance to counter this threat. (desktop sharing apps and email links/attachments)
Monitoring remote access with strong access-based policies (identity and access management)
Further, cybersecurity experts suggest the following ways to mitigate Ransomware attacks:
Having a backup and disaster recovery plan
Updating OS, antivirus and other software on a timely basis
Multi-factor authentication and access protocols
Email protection for phishing attacks
Web Protection against malware, spear-phishing and new strands of Ransomware
Securing endpoints with endpoint detection and response (EDR)
The best protection is to create cyber awareness at both organizational as well as individual levels. As most Ransomware attacks start with phishing and thus, basic security hygiene and awareness can go a long way in keeping these attacks at bay.
Takeaway
Threat landscape is evolving at breakneck speed posing novel challenges to businesses. Overall, Ransomware continues to be the top threat attack type in most sectors. Businesses ought to have the right layers of cyber protection and security skills/resources to strengthen their digital defenses against coming-of-age and emerging Ransomware threats.
Media Contact
Email: [email protected]
Disclaimer: All the information, views and opinions expressed in this op-ed are those of the authors and their respective web sources and in no way reflect the views, principles, or objectives of Futurism Technologies.
Futurism Technologies is a trusted Digital Transformation (DX) advisor and consulting partner helping businesses around the world to unlock the true value of digital for the last two decades. One of the fastest-growing global digital transformation companies with offices across continents including North America, Europe, the Gulf, Asia, and Australia, Futurism delivers 360-degree Digital Transformation solutions to enterprises of all sizes and verticals. We have been helping enterprises leverage advanced technologies with our tested DX solutions. Futurism takes great pride in helping businesses realize the true potential of digital by helping them leverage the most from coming-of-age technologies such as Artificial Intelligence (AI), Machine Learning (ML), Robotic Process Automation (RPA), 5G, IoT, Data Science/Big Data, Cybersecurity, Blockchain, Mobility, Product Engineering, Cloud, and more.
Make your business more successful with latest tips and updates for technologies