Backdoors surpassed Ransomware as the Top Attack Vector in 2022
The evolution of malware has made deployment of backdoors on a company’s networks a cakewalk for cyber attackers.
Backdoors surpassed Ransomware attacks as the top attack types in 2022. Though Ransomware has been dominating the cybersecurity threat landscape for years, a recent security report by CrowdStrike has revealed a startling fact that backdoor deployment is the most common tactic used by cybercriminals these days.
The CrowdStrike report analyzed more than 300 cyber incidents in 2021 and 2022, and found that 90% of the attacks involved the use of backdoor deployment. Backdoors are essentially hidden entry points that allow cyber attackers to bypass security measures and gain access to networks and systems. Once attackers have the access, they can carry out a range of malicious activities including data theft, espionage, and further network exploitation.
Read also: Uber suffers major cyberattack! Sensitive Data of Millions Exposed
According to the report, the rapid shift towards backdoor deployment is likely due to the increased adoption of advanced email protection from malware and Ransomware attacks, Ransomware-resistant backups and other defensive measures deployed by organizations. Attackers are therefore resorting to backdoor deployment as a way to gain access and breach into vulnerable systems and networks.
The report also highlighted the rise in the use of sophisticated techniques used by attacker, with many employing new strands of custom malware and other advanced attack tactics to evade detection and breach into systems and networks. Attackers are coming up with evolving tactics, procedures and techniques in the already inflated attack surface, making it increasingly challenging for organizations to defend against these threats.
The report’s findings underpin the importance of proactive and advanced threat protection measures for organizations. This includes regular security assessments, employee training, insider threat detection, email and web security, endpoint security, identity and access management for strong access controls, data protection and monitoring, network segmentation, etc. Additionally, it highlights the need for organizations to stay vigilant and agile in their response to emerging threats.
What we observed?
There was a 17% surge in malware attacks targeting the oil and gas, transportation and manufacturing sectors. In light of this, Futurism recommends taking measures to prevent known USB-based malware programs (like Raspberry Robin) from infiltrating security tools. This includes providing security awareness training and disabling autorun features for removable media.
The report noted a growing popularity among developers for the Rust programming language, with advanced malware versions that can retrieve sensitive device information, including credit card data, usernames, passwords, and files, as well as capture screenshots of the user’s desktop or steal Cryptocurrency wallets for Bitcoin, Ethereum, etc.
Read also: Twitter’s ‘Blue Tick’ Chaos Triggers New Spear Phishing Campaign
As backdoor deployment becomes increasingly common, Futurism recommends organizations to prioritize threat intelligence and incident response capabilities to quickly detect and respond to attacks and breaches. With cybercrime on the rise, Futurism suggests businesses to take proactive steps to protect themselves against the evolving threat landscape.
Nearly 65% of backdoor breaches were unsuccessful attempts!
However, as attackers continue to innovate and unleash new-age backdoor attack tactics, they are likely to develop and invent sophisticated and difficult-to-detect methods. This could result in backdoor attacks becoming the next Ransomware crisis. To prevent this, it is crucial for organizations to improve their threat intelligence game and gain a better understanding of how the bad actors operate.
One way to stay ahead of the curve is by leveraging advanced threat intelligence – SIEM solution powered by AI and market-winning security automation to predict and respond to threats more quickly and intelligently. A managed cyber security services provider can help you deploy the right layers of security and resources to respond to threats proactively, reduce downtime, and protect data.
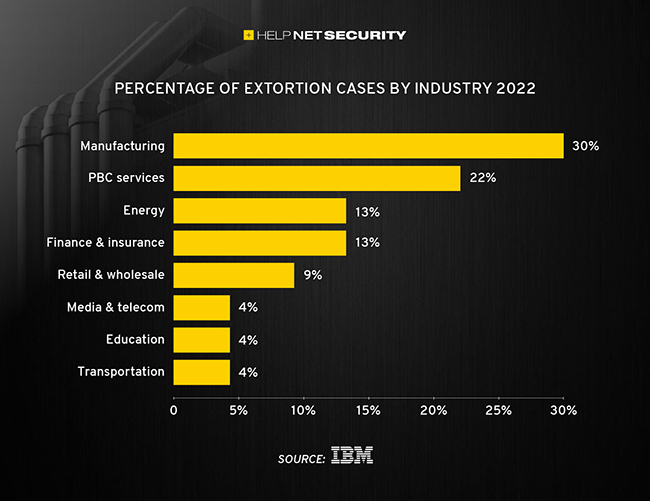
Manufacturing continues to be the most targeted industry followed by finance, insurance and healthcare. According to the IBM Threat Intelligence Report more than 25% of cases observed in the manufacturing sector were the result of backdoor deployment. As per the report’s findings, backdoor deployment was the primary method used by Ransomware attackers in these breaches, since manufacturing organizations just cannot afford downtime. Further, spear phishing was the chief cause for initial access in most industries. This includes use of suspicious attachments and links.
Read also: Major Engineering Company Hit by Ransomware Attack, Halts Operations!
How to secure your business?
Futurism makes five smart recommendations to help businesses secure their systems, networks and data from backdoor attacks.
Be Cyber Smart:
Prioritize data security: The key to preventing these types of attacks is to acknowledging as what data matters the most to your business. Managing and securing databases is one of the most challenging issues faced by organizations today. This is why Futurism recommends having a Zero Trust Security Framework in place to stay ahead of the threats.
Identify your weak spots: Identify your weak or vulnerable areas or backdoors that the attackers are most likely to target. Deploy a robust vulnerability assessment and penetration testing (VAPT) mechanism in place.
Think like threat actors: Try to identify and learn the attack tactics, procedures and sophistication used by attackers. For instance, the attack tactics used on a healthcare company will be miles apart from what they might use for a manufacturing company.
Maintain optimum visibility of your endpoints: Ensure to have optimum visibility into all your mission-critical and connected endpoints including mobiles, connected devices (IoT), desktops, laptops, etc. with the help of a powerful endpoint security solution.
Deploy threat intelligence: Assess common attack patterns and tactics used by hackers. Assess common attack patterns and tactics used by hackers. Deploying threat intelligence will provide up-to-the-minute protection from new threats including new strands of malware and Ransomware.
Be it security skills shortage or tackling new bad actors to prevent backdoor attacks, roping in the service of a trusted security services provider will not only help you deploy a robust line of defense, but will also help you strengthen your security posture.
Disclaimer: All the views and opinions expressed in this article are those of their respective web authors and sources in no way reflect the views, objectives, or principles of Futurism Technologies.
Futurism Technologies is a trusted Digital Transformation (DX) advisor and consulting partner helping businesses around the world to unlock the true value of digital for the last two decades. One of the fastest-growing global digital transformation companies with offices across continents including North America, Europe, the Gulf, Asia, and Australia, Futurism delivers 360-degree Digital Transformation solutions to enterprises of all sizes and verticals. We have been helping enterprises leverage advanced technologies with our tested DX solutions. Futurism takes great pride in helping businesses realize the true potential of digital by helping them leverage the most from coming-of-age technologies such as Artificial Intelligence (AI), Machine Learning (ML), Robotic Process Automation (RPA), 5G, IoT, Data Science/Big Data, Cybersecurity, Blockchain, Mobility, Product Engineering, Cloud, and more.
Make your business more successful with latest tips and updates for technologies