Futurism Cybersecurity Services
Futurism’s Cybersecurity suite is a full stack of cyber security services designed to offer round-the-clock protection against coming-of-age cyber threats.
Sep 2021
Deliver secure experiences across all device types with Futurism UEM solutions and MDM services.
Services \ Cyber Security \ UEM & MDM Services
Futurism Unified Endpoint Management solutions and Mobile Device Management solutions help businesses and IT teams spend less time and effort in managing and securing all their mobile and mission-critical endpoints.
Futurism’s Mobile Device Management solutions including Unified Endpoint Management solutions ensure optimum protection against coming-of-age mobile threats with market-leading endpoint threat and mobile device defense technology powered by IBM. Our MDM services engineers and analysts leverage best-of-breed threat intel and work 24/7 to protect all your critical mobile endpoints helping you improve your security posture by leveraging a zero-trust security architecture.
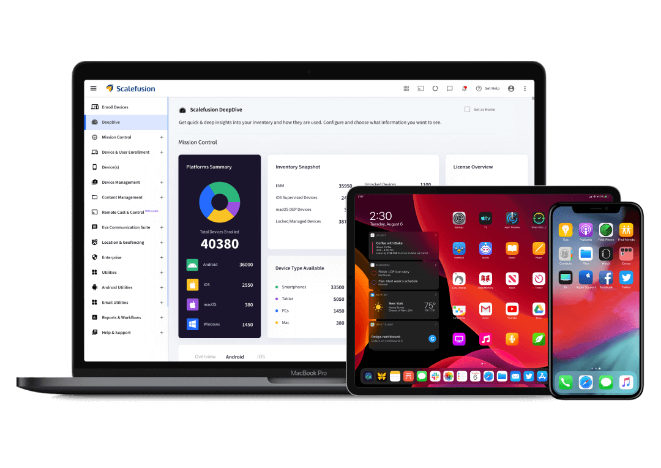
Enforce company security policy across all devices, multiple platforms, and OS versions with our proven mobile device management solutions.
Our mobile device management solutions enable you to manage and control data, network, and configuration settings for any device in the network.
Futurism mobile device management solutions and UEM services enable you to control the content viewed on browsers of all your managed and connected devices.
Manage and secure all the apps running on your devices in the network with our MDM services. Monitor suspicious apps in real-time.
Futurism MDM services help to track real-time location, create virtual boundaries, and track the browsing activity/behavior of all your devices. Get alerts when a device enters or exits a geo-fence with powerful mobile device management solutions.
Get improved control over individual and group devices with our unified endpoint management solutions. Futurism UEM solutions help you to secure all endpoints and mobile devices including mission-critical corporate apps (calling and messaging) and data.
Futurism unified endpoint management solutions render unmatched BYOD capabilities to not only secure devices and apps on the go, but also offer intelligent and real-time analytics into compromised devices.
A powerful line of cyber defense in the age of advanced and sophisticated threats.

A powerful line of cyber defense in the age of advanced and sophisticated threats.













A powerful line of cyber defense in the age of advanced and sophisticated threats.




According to a recent cybersecurity advisory released by the American Hospital Association (AHA), health care organizations across the U.S...





Make your business more successful with latest tips and updates for technologies